Increasingly, attackers don't hack in anymore—they log in. As enterprises rapidly adopt cloud-based SaaS applications, our security landscape has fundamentally shifted. Identity, not infrastructure, has become the primary target.
Why Identity Is the New Battlefield
To understand the scale of this identity crisis, let's look at the data:
- In 2024, credential-based attacks remain the leading cause of data breaches, responsible for ~38% of incidents, significantly outpacing phishing (~17%) and exploits (~16%). While phishing is often reported separately, it primarily serves as a vehicle to steal credentials.
- Once attackers obtain credentials, they target web applications (~50% of cases) rather than VPNs or remote desktop solutions. This is a problem because cloud-based apps often have limited security visibility, a growing risk as organizations now use an average of 112 SaaS apps—up from just 16 in 2017.
- 77% of SaaS application attacks (a subset of web app attacks) begin with stolen credentials.
This focus on identity-based attacks is amplified by two emerging trends:
- The Rise of Shadow Identities: Employee-driven SaaS adoption has outpaced IT oversight, resulting in unmonitored accounts across organizations. These "shadow identities" represent a growing blind spot in enterprise security, making it harder to track and secure access points.
- The Ghost Login Problem: SaaS platforms typically offer multiple authentication methods to reduce friction. When employees sign up with basic credentials before IT can establish proper identity management, it can create a dangerous scenario called "Ghost Login"—where accounts become susceptible to takeover through dual authentication paths.
The Snowflake Incident: A Warning Sign
To understand how these identity vulnerabilities play out in real-world scenarios, we can look at the recent incident involving a cloud software provider. This incident, which led to millions of records in data exposure for 165 organizations, exposed a dangerous intersection of vulnerabilities that could threaten many SaaS platforms. The attackers exploited three critical weaknesses that exist across today's SaaS landscape, one of which aligns with Ghost Logins:
- Compromised credentials—some dating back to breaches from 2020.
- Weak or absent MFA: Some victims were susceptible to Ghost Login attacks due to the availability of multiple authentication avenues.
- Widespread application adoption.
This recipe for compromise is particularly troubling because these three elements are present in so many SaaS applications today. The question isn't if another SaaS platform will be targeted but when.
Why Traditional Security Falls Short
Today's identity-centric security challenges have outpaced legacy tools designed for network and endpoint protection. With 83% of SaaS applications managed outside IT control and organizations adding four new tools monthly, businesses face a growing maze of unmonitored "shadow identities." The rise of cloud applications accessed through browsers and widespread credential sharing across devices has created security risks that traditional approaches simply cannot address.
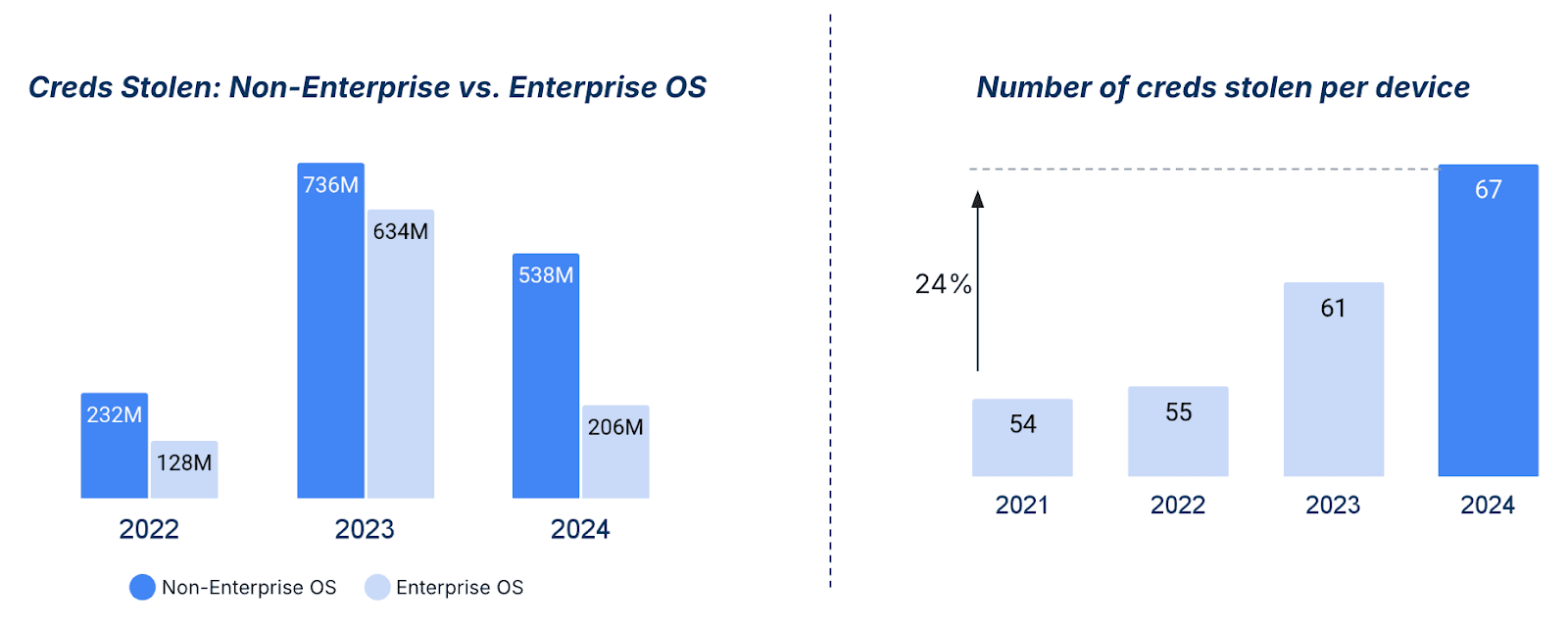
Recorded Future's Identity Intelligence shows that personal devices are more frequently targeted than corporate ones, with more credentials being harvested per device than ever before. This vulnerability stems from the growing demand for convenience—modern browsers and SaaS applications sync our credentials across devices, expanding the attack surface in ways that traditional security measures were never built to handle.
Building a Modern Defense
In light of these trends, security teams can focus on two immediate actions to improve their organization’s risk profile:
- Implement continuous monitoring for compromised credentials
- Enable automatic password resets when leaks are detected
Recorded Future’s Identity Intelligence delivers real-time detection and automated remediation of compromised credentials across your workforce and customer base, helping security teams prevent account takeovers before they impact the business.
For the long term, organizations can deploy adaptive MFA. This approach automatically adjusts authentication requirements based on risk by analyzing contextual factors like location, device health, and user behavior. When properly implemented, adaptive MFA can strengthen identity security while minimizing friction for legitimate users, helping organizations better defend against credential-based attacks.