What is a virtual firewall?
A virtual firewall is a firewall device or service that provides network traffic filtering and monitoring for virtual machines (VMs) in a virtualized environment. Like a traditional network firewall, a virtual firewall inspects packets and uses security policy rules to block unapproved communication between VMs. A virtual firewall is often deployed as software or a virtual appliance.
Virtual firewalls are commonly used to protect virtualized environments because they're the least expensive and the most portable, due to the ease of moving a virtual firewall from cloud to cloud. A virtual firewall is also simple to upgrade and maintain.
How a virtual firewall works
A virtual firewall, also known as a cloud firewall or a firewall as a service, operates like a physical firewall but does so in a virtualized environment.
A virtual firewall works in two modes -- bridge mode and hypervisor mode. Similar to a traditional firewall system, bridge mode works by diagnosing and monitoring all of a VM's incoming and outgoing traffic. In hypervisor mode, the virtual firewall operates in isolation from the physical network, residing in the core hypervisor kernel and managing the incoming and outgoing traffic of the VM. The following is an overview of the functions of a virtual firewall:
- Packet inspection. A virtual firewall is an application or cloud network firewall service that provides packet filtering within a virtualized environment. When data packets traverse the virtualized network, the virtual firewall intercepts them and examines their headers for various attributes, such as source and destination IP addresses, ports, protocols and payload content. This interception enables the firewall to either block the packets or let them pass through the network. Many complex virtual firewalls also come with deep packet inspection features that are used to analyze packet contents and detect malware agents.
- Traffic management. A virtual firewall manages and controls incoming and outgoing traffic. It works in conjunction with switches, routers and servers similar to a physical firewall. Virtual firewalls can identify anomalies and potential security threats by analyzing network traffic patterns and behaviors.
- Prevention of unauthorized access. A virtual firewall prevents an unauthorized user from accessing and transmitting data and files and stops an organization's employees from transferring any sensitive data or documents.
- Logging and reporting. Virtual firewalls log information about enabled and blocked traffic, as well as any security incidents or detected anomalies. These logs are beneficial for troubleshooting, security analysis and compliance reporting.
- Network segmentation. By dividing the network into separate segments or zones, virtual firewalls create barriers that restrict the lateral movement of threats. This containment strategy helps mitigate security incidents and limit their effects on the overall network.
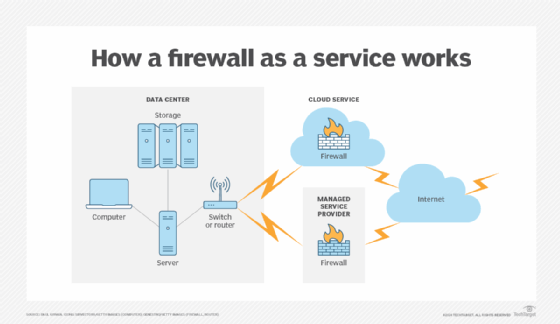 A firewall-as-a-service configuration houses virtual firewalls in either a cloud service provider's or a managed service provider's facility.
A firewall-as-a-service configuration houses virtual firewalls in either a cloud service provider's or a managed service provider's facility.
Benefits of virtual firewalls
A virtual firewall serves many different purposes, especially in modern network security and cloud computing. The benefits of virtual firewalls include the following:
- Enable optimization for specific network requirements. Virtual firewalls can be customized to meet specific network requirements. For example, administrators can define rules inside these firewalls to govern how traffic is inspected, filtered and controlled. They can also undergo performance tuning and seamlessly integrate with the existing security infrastructure and security services.
- Provide flexibility and scalability. Virtual firewalls scale and adapt to changing network requirements as they can dynamically allocate resources based on network demand. This scalability ensures that virtual firewalls remain effective in meeting the evolving needs of the network.
- Permit north-south traffic inspection. Cloud-based resources extend beyond the conventional corporate network perimeter, making them directly reachable from the public internet. To safeguard these cloud-based resources from compromise and possible data leaks, a virtual firewall appliance must be deployed to analyze and filter incoming and outgoing traffic.
- Allow east-west traffic inspection. East-west data flow refers to the movement of data between servers, devices or services within the same network or data center. When cybercriminals breach an organization's network, they often move laterally to access sensitive resources and accomplish their goals. As more sensitive data and functionalities are hosted in the cloud, it's crucial to inspect content and enforce security policies on east-west traffic flows to safeguard cloud-based resources. This highlights the necessity of a virtual firewall.
- Provide full visibility. Virtual firewalls provide full visibility into network traffic by inspecting packets, generating logs, analyzing traffic patterns, integrating with security tools, offering centralized management and providing customizable dashboards and reports. Also, advanced virtual firewalls seamlessly integrate with public clouds, incorporating metadata for enhanced context. They achieve this by employing a tag-based policy model, which is a method of applying security policies and rules to resources in a cloud environment based on metadata tags assigned to those resources. Virtual firewalls also provide other capabilities such as tight integration with major cloud service providers and offering a flexible policy framework that can adapt to dynamic environments.
- Offer ease of deployment. Deploying virtual firewalls is easy due to their software-based design and compatibility with popular virtualization platforms, including VMware and Microsoft Hyper-V. They can be quickly deployed as virtual appliances onto existing infrastructure without specialized hardware and with preconfigured templates or virtual machine images. Integration with automation tools further enhances deployment efficiency, minimizing manual intervention and the risk of errors.
- Provide cost-effectiveness. Virtual firewalls are less expensive to upgrade and maintain compared to traditional hardware firewalls, making them a cost-effective option for protecting virtualized environments and cloud resources.
- Offer compatibility with any cloud infrastructure. Virtual firewalls aren't tied to a specific cloud provider and can operate seamlessly across different public cloud environments, including Amazon Web Services (AWS), Microsoft Azure, Google Cloud, Oracle Cloud and Alibaba Cloud. This flexibility enables organizations to deploy virtual firewalls consistently regardless of their chosen cloud infrastructure, promoting interoperability and ease of management across diverse cloud environments.
- Enable private cloud deployments. Virtual firewalls are helpful tools for private cloud environments. They offer features including scalability, automated deployment and dynamic object and policy administration that facilitate private cloud deployment and security.
Virtual firewalls vs. physical firewalls
Both virtual and physical firewalls serve the same fundamental purpose of protecting networks from unauthorized access and security threats. However, they differ in their characteristics and how they are deployed.
The following are some pros and cons as well as differences between physical and virtual firewalls:
Physical firewalls
- A physical firewall -- sometimes known as a hardware firewall -- is a network firewall deployed in a real-world security appliance or as part of a routing device that's situated at the edge of the network or between environments.
- A physical firewall connects to the protected internal network and the public internet -- or some other unprotected or external network -- over dedicated network interfaces. It consists of servers and switches and works outside an operating system as opposed to being built-in. The servers are connected to designated switches and then routed to the firewall.
- One of the benefits of using a hardware or physical firewall is that it's situated between the server and the internet, and it's the only way for network traffic to pass to and from the protected network. Without passing traffic through the network interfaces, the hosts, servers and other devices on the internal protected network won't be able to communicate or exchange data with any hosts, servers or other devices on the public internet. Threats are reduced because all data exchanges go through the firewall before they can be completed.
- Another advantage of using physical firewalls is that hardware security appliances are designed to handle heavier traffic loads and have faster response times. Network perimeters can also be strengthened using a physical firewall, improving network security.
- A physical firewall is easier to manage because it's an isolated network component and doesn't affect the performance of other applications, as it might in a virtualized environment. A hardware firewall can also be shut down, moved or reconfigured with little effect on network connectivity or performance.
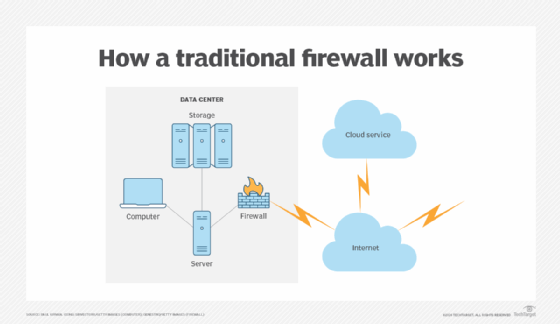 This configuration shows a firewall in a traditional physical network.
This configuration shows a firewall in a traditional physical network.
Virtual firewalls
- In contrast to physical firewalls, virtual firewalls are deployed as software appliances running within virtualized environments. A virtual firewall monitors and protects network traffic by transiting virtual switches and other virtual machines.
- Virtual switches link systems and applications across logical partitions and a hypervisor manages the virtualized environment. When virtual firewalls are installed on individual servers, they can be configured and set up more easily.
- Virtual firewalls can also be less expensive than physical firewalls, but the cost of purchasing and deploying a large number of virtual firewalls can still be significant. However, virtual firewalls reduce operational costs, since they eliminate the necessity for physical upgrades or maintenance.
- Virtual firewalls also deliver a fraction of the network throughput dedicated physical firewalls can provide, which can create bottlenecks throughout the network and reduce business agility and performance.
- Another advantage of virtual firewalls over hardware-based firewalls is that they can be centrally administered, while hardware firewalls often need IT and network support staff to install, administer and support them on-site.
Security and virtual firewall
Using a virtual firewall in the cloud can help protect an organization's cloud infrastructure and services by running in a virtual data center on an organization's servers in an infrastructure as a service or platform as a service model. This type of firewall application runs on a virtual server and protects traffic going to, from and between applications in the cloud.
A cloud-based virtual firewall can meet several network and cybersecurity requirements in the cloud, including the following:
- Policy-based filtering. A virtual firewall secures the virtual data center using policy-based filtering and managing traffic flowing to or from the internet, between virtual networks or between tenants.
- Securing connectivity between cloud and physical infrastructure. Virtual firewalls secure the physical data center by extending it to the cloud. This is especially applicable to organizations migrating applications to the cloud that need secure connectivity between the cloud and their local infrastructures.
- Securing remote access. Virtual firewalls secure remote access by offering the advanced access policy, filtering and connection management needed to provide clients with access to the cloud.
- Consistent data protection. Virtual firewalls ensure that all data is subject to the same protective measures as on-premises, hardware-based firewalls.
- Integration with service providers. Virtual firewalls maintain the integrity and confidentiality of applications and data by integrating with access control providers and offering a wide variety of granular, policy-based filtering tools.
- Rapid response to changing security requirements. Virtual firewalls protect applications and assets in their virtualized environments, as well as respond rapidly when network security requirements change in remote or branch offices, as well as accommodate temporary staff deployments.
- IoT security features. Many high-end, next-generation firewalls also offer internet of things (IoT) security features specifically designed for IoT environments. These features provide visibility into unmanaged devices, detect behavioral anomalies and offer risk-based policy recommendations.
- Additional networking functions. Some virtual network firewalls integrate additional networking functions, such as site-to-site and remote access virtual private networks, quality of service and URL filtering.
- Content-based decision-making. Virtual firewalls can examine the content of applications and decide which requests, regardless of port number, should be permitted. This functionality empowers organizations to thwart a wide array of attacks including distributed denial-of-service attacks, HTTP floods and SQL injections.
- Malware protection. By using different methods of analysis, such as machine learning (ML) and dynamic analysis, virtual firewalls can detect and mitigate certain file-based threats. This can also involve signature-based detection methods to defend against emerging threats.
- Domain name systems (DNS) security. Virtual firewalls can employ predictive analytics and ML to prevent attacks that exploit DNS.
Learn about evolving cloud-based attacks as more and more businesses store critical data on the cloud. Use cloud threat intelligence to stay aware of potential attacks and protect assets from attackers who are always changing their attack tactics.
This was last updated in May 2024
 8 months ago
35
8 months ago
35






