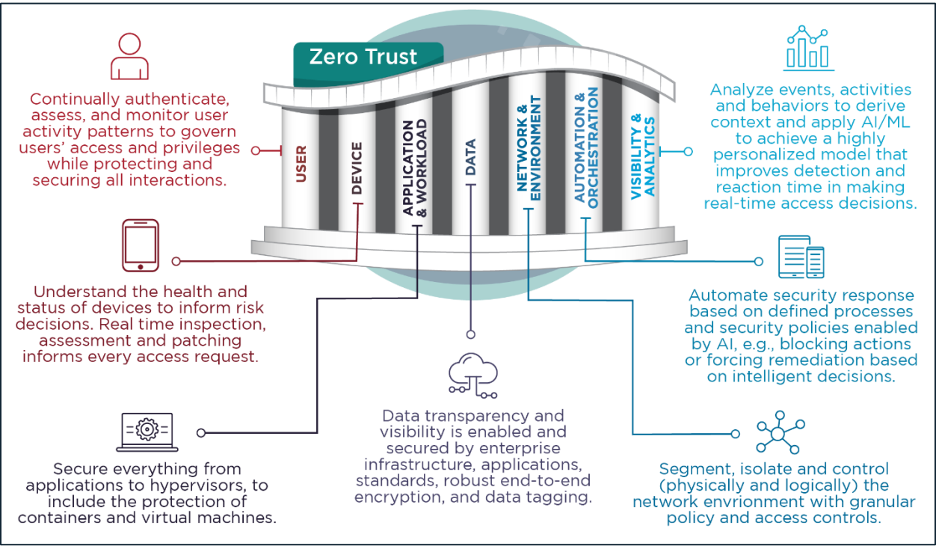
A zero trust architecture (ZTA) model comprises seven pillars to enhance the security posture of all organizations, from government agencies to private sector enterprises. ZTA is a set of system design principles with a security model in mind. It includes an advanced cybersecurity strategy because threats can come from inside or outside of a network boundary. Each pillar of the model has details on the measures needed to secure an environment.
ZTA is shifting the “trust but verify” paradigm into “never trust, always verify.” This is due to the innumerable attacks and malicious attempts to exploit sensitive information. According to the 2024 Global CISO Report, 72% of organizations have experienced a security incident in the last two years. Ensuring secure and protected application data is becoming more important than ever.
US government and zero trust: The NSA’s guidance
Maintaining secure data is especially critical for government agencies that safeguard national security information. Executive Order 14028 made ZTA mandatory for civilian agencies in the executive branch of the United States government. The order emphasizes the importance of deterring, identifying, and responding to bad actors. These agencies must strike a balance between maintaining a sophisticated security strategy while modernizing applications and advancing to the cloud.
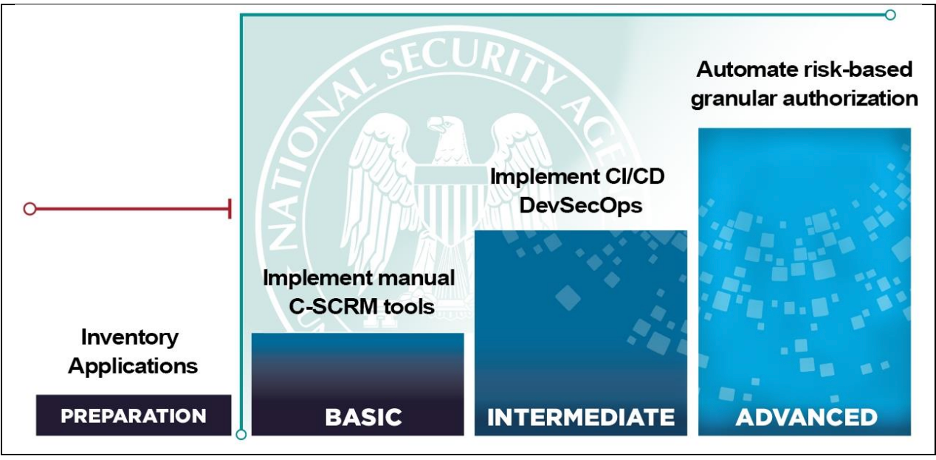
The National Security Agency (NSA) recently provided guidance on advancing the maturity of the application and workload pillar, illustrated below. The NSA advocates that properly securing the application layer and the supporting infrastructure is central to adopting ZTA.
 NSA – Advancing Zero Trust Maturity Throughout the Application and Workload Pillar https://media.defense.gov/2024/May/22/2003470825/-1/-1/0/CSI-APPLICATION-AND-WORKLOAD-PILLAR.PDF
NSA – Advancing Zero Trust Maturity Throughout the Application and Workload Pillar https://media.defense.gov/2024/May/22/2003470825/-1/-1/0/CSI-APPLICATION-AND-WORKLOAD-PILLAR.PDFThe NSA also released a cybersecurity information sheet (CSI) which outlines a tiered approach for the applications and workload pillar. In the CSI, the NSA suggests that agencies “[with] robust identity management for authorized users and [who] have integrated continuous automated monitoring into their security strategy will have full visibility to trace every transaction and pinpoint exactly what each workload is doing at any given moment.”
The application and workload pillar
The goal of the application and workload pillar is to secure access and prevent unauthorized data collection or interference with mission critical systems.
A mature application and workload pillar focuses on the following five key capabilities:
- Inventorying. Taking an inventory of the applications within an agency’s network is crucial to prioritize the cybersecurity posture for integral systems.
- A DevSecOps framework. Automating vulnerability analysis is a key component of DevSecOps, a recommended framework by the ZTA model. Source code and third-party libraries need to be vetted during the development process using continuous integration/continuous delivery. When security is part of the entire process, organizations can mitigate the risk of vulnerabilities.
- Software risk management. Many agencies use commercial off-the-shelf (COTS) applications that could include vulnerabilities and other risk factors. Agencies must understand the risks associated with COTS products before they reach production. These applications include inherent danger when they are not properly vetted.
- User access. Agencies should implement the principle of least privilege and constantly analyze resource authorization and integration.
- Continuous monitoring. Agencies should continuously monitor applications for any changes. Dashboards and alerts need to be available for notifying an agency if there has been a new vulnerability introduced.
 NSA – Advancing Zero Trust Maturity Throughout the Application and Workload Pillar https://media.defense.gov/2024/May/22/2003470825/-1/-1/0/CSI-APPLICATION-AND-WORKLOAD-PILLAR.PDF
NSA – Advancing Zero Trust Maturity Throughout the Application and Workload Pillar https://media.defense.gov/2024/May/22/2003470825/-1/-1/0/CSI-APPLICATION-AND-WORKLOAD-PILLAR.PDFFortifying zero trust architecture with observability
With the new guidance, US government agencies are encouraged to strengthen their application and workload security to ensure secure data and protection from risks.
The Dynatrace platform’s unified approach to observability, security, and business analytics enables teams to take a proactive approach to securing applications and sensitive data. The platform automatically identifies critical workloads using the SmartScape technology and provides end-to-end observability into transactions for understanding what the application is doing at any given time. For example, another pillar of ZTA is visibility and analytics, which both act as the “glue” that holds all the other pillars together. Dynatrace is that glue, providing granular visibility into every application, instance, and container to catch vulnerabilities before they reach production along with real-time insights to inform data-driven decisions.
Dynatrace has code-level visibility into each transaction, which enables Runtime Vulnerability Analytics (RVA). RVA empowers teams with the ability to detect, visualize, analyze, monitor, and remediate open-source and third-party vulnerabilities, as well as the security vulnerabilities in libraries and first-party code in production and pre-production environments at runtime. If one of those vulnerabilities is compromised, Dynatrace Runtime Application Protection can detect and block attacks automatically and in real time.
The journey to zero trust architecture maturity is ongoing, and Dynatrace is here to help government agencies adapt to emerging threats and challenges.
Agencies should review the NSA’s guidance for Advancing Zero Trust Maturity Throughout the Application and Workload Pillar to understand the benefits of observability for zero trust architectures. Proactive visibility across the pillar will enable a stronger posture to counteract threats.
To learn more about how Dynatrace observability and security bridges the gap in achieving CISA/DoD zero trust pillars, download the free ebook: Achieving zero trust with observability.
 5 months ago
39
5 months ago
39