The two primary takeaways from a new Q3 ‘API Threatstats’ report are: firstly, the number of API vulnerabilities is growing rapidly; and secondly, because of this rapid growth, a new ‘real-time, data driven compilation of the top ten API security threats’ is required.
The greater part of the report (PDF) from API and app security firm Wallarm discusses the individual vulnerability categories with real life examples of where they have been used. For example, the discovery of vulnerabilities in widely-used OAuth and SSO protocols, exposing potential security breaches in systems from major firms like Cisco and Ivanti – but it is the new approach to threat listing that is the standout feature.
Wallarm’s Top 10 API threats is presented in the same format as the better-known OWASP Top Ten. This approach serves two purposes: it provides a format that is already well known and understood in cybersecurity, and it also highlights the differences between the two methodologies. While OWASP publishes its list perhaps once every four years, Wallarm intends to publish its own list four times every one year. This may not be genuinely real-time, but it is certainly more dynamic.
Wallarm’s justification for this new listing is drawn from the rapid growth of new API vulnerabilities. “We discovered 239 new vulnerabilities, of which 59 related to the category of injections,” Girish Bhat, Wallarm’s VP of marketing told SecurityWeek. He contends that this makes injections the #1 API threat — OWASP does not give injections such priority. Bhat’s conjecture is that the greater the number of vulnerabilities, the greater the risk posed by that category of vulnerability.
The growth of new vulnerabilities has a second effect demanding a more dynamic approach than is possible with the OWASP approach. Wallarm has detected 13 new vulnerabilities associated with ‘weak secrets and cryptography’ (issues such as hard coded secrets or weak encryption algorithms), and nine vulnerabilities associated with ‘sessions and password management’ (such as inadequate session handling and poor password management schemes).
Neither of these categories are discussed in the OWASP list — the incidence of new vulnerabilities occurs at a faster rate than can be covered by the slow and steadfast approach available to the OWASP community. True coverage of current API threats demands the type of list put forward in the Wallarm study, which it calls ‘real-time’ opposed to OWASP’s static list.
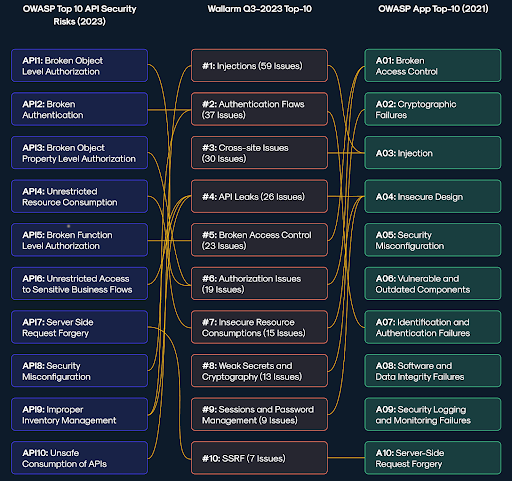
Wallarm does not suggest that OWASP should be ignored, but that its insights should be extended with a more current view of the API threatscape. “Established security frameworks, like OWASP API Security Top-10, are one way to get started but have limitations in addressing today’s complex API security needs,” says Ivan Novikov, CEO at Wallarm. “This real-time data-driven threat list complements and extends the OWASP framework by identifying unaddressed threats and vulnerabilities, enhancing overall security posture.”
It is, however, a stretch to call a list published once every three months ‘real-time’. Both the OWASP and the Wallarm top ten lists are effectively snapshots in time – although Wallarm’s snapshot will tend to be more closely aligned with the current situation.
However, it is still possible to get a genuine real-time view of Wallarm’s position via its website. This is available whether you are a Wallarm customer or not: the Wallarm Playground.
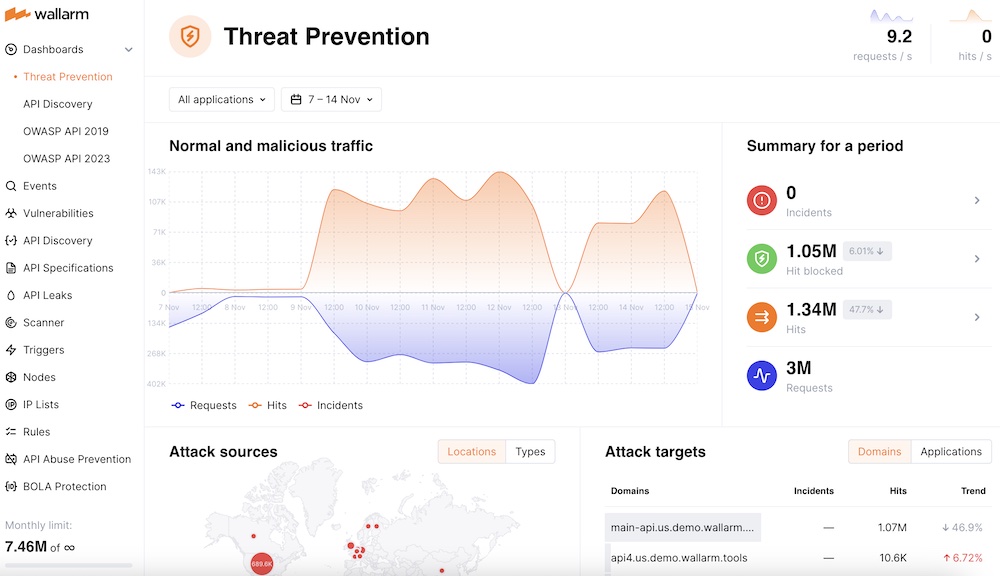
The Playground gives a genuinely real-time view of API attacks, including hotspots and type of attack. Current attacks can then be related to the taxonomy of vulnerabilities described in the Wallarm report, and defenders can better judge and tailor their defensive posture to suit the actual and current API threatscape.
Related: Applying AI to API Security
Related: Ivanti Ships Urgent Patch for API Authentication Bypass Vulnerability
Related: API Flaw in QuickBlox Framework Exposed PII of Millions of Users
Related: SIEM and Log Management Provider Graylog Raises $39 Million
 11 months ago
66
11 months ago
66