
GagoDesign via Shutterstock
The group behind a sophisticated remote access Trojan, SilverRAT, has links to both Turkey and Syria and plans to release an updated version of the tool to allow control over compromised Windows systems and Android devices.
According to a threat analysis published on Jan. 3, SilverRAT v1 — which currently works only on Windows systems — allows the building of malware for keylogging and ransomware attacks, and includes destructive features, such as the ability to delete system restore points, researchers from Singapore-based Cyfirma stated in their analysis.
SilverRAT Builder Allows Various Features
SilverRAT shows that the region's cybercriminal groups are becoming more sophisticated, according to Cyfirma's analysis. The first version of SilverRAT, whose source code was leaked by unknown actors in October, consists of a builder that allows the user to construct a remote access Trojan with specific features.
The more interesting features, according to Cyfirma's analysis, include using either an IP address or webpage for command and control, bypasses for antivirus software, the ability to erase system restore points, and the delayed execution of payloads.
At least two threat actors — one using the handle "Dangerous silver" and a second using "Monstermc" — are the developers behind both SilverRAT and a previous program, S500 RAT, according to Cyfirma's analysis. The hackers operate on Telegram and through online forums where they sell malware-as-a-service, distribute cracked RATs from other developers, and offer a variety of other services. In addition, they have a blog and website called Anonymous Arabic.
"There are two people managing SilverRAT," says Rajhans Patel, a threat researcher with Cyfirma. "We have been able to gather photographic evidence of one of the developers."
Starting From Forums
The group behind the malware, dubbed Anonymous Arabic, is active on Middle Eastern forums, such as Turkhackteam, 1877, and at least one Russian forum.
In addition to the development of SilverRAT, the group's developers offer a distributed denial-of-service (DDoS) attacks on demand, says Koushik Pal, a threat researcher with the Cyfirma Research team.
"We have observed some activity from Anonymous Arabic since late November 2023," he says. "They are known to be using a botnet being advertised on Telegram known as 'BossNet' to conduct DDOS attacks on large entities."
While the Middle East threat landscape has been dominated by the state-run and state-sponsored hacking groups in Iran and Israel, homegrown groups such as Anonymous Arabic continue to dominate the cybercrime markets. The ongoing development of tools such as SilverRAT highlight the dynamic nature of the underground markets in the region.
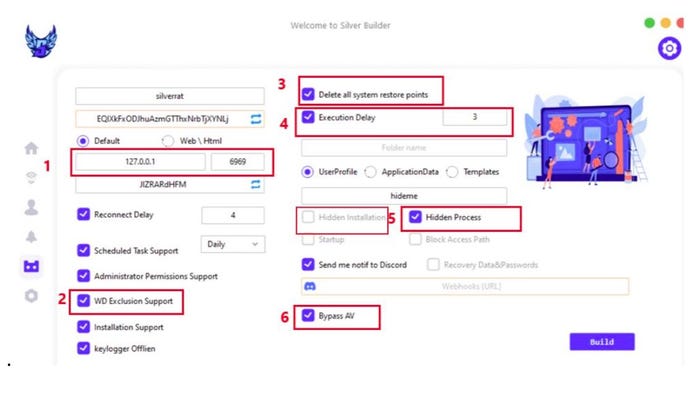
The SilverRAT dashboard for building trojans. Source: Cyfirma
Hacking groups in the Middle East tend to be quite varied, says Sarah Jones, a cyber threat intelligence research analyst at managed detection and response firm Critical Start, who cautioned that individual hacking groups are constantly evolving and generalizing their characteristics can be problematic.
"The level of technical sophistication varies greatly among groups in the Middle East," she says. "Some state-backed actors possess advanced capabilities, while others rely on simpler tools and techniques."
A Gateway Through Game Hacks
Of the identified members of the Anonymous Arabic group, at least one is a former game hacker, according to data gathered by researchers at Cyfirma, including the Facebook profile, YouTube channel, and social-media posts of one of the hackers — a man in his early 20s who lives in Damascus, Syria, and started hacking as a teenager.
The profile of young hackers who cut their teeth on finding exploits for games transcends the hacking community in the Middle East. Teenagers starting their hacking careers by creating gaming hacks or launching denial-of-service attacks against game systems has become a trend. Arion Kurtaj, a member of the Lapsus$ group, started as a Minecraft hacker and later moved on to hacking targets such as Microsoft, Nvidia, and game maker Rockstar.
"We can see a similar trend with the developer of SilverRAT," says Rajhans Patel, a threat researcher with Cyfirma, adding in the threat analysis: "Reviewing the developer's previous posts reveals a history of offering various first-person shooter (FPS) game hacks and mods."
The US Department of Homeland Security's Cyber Safety Review Board (CSRB), which conducts post-mortem analysis of major hacks, identified the continuing pipeline from juvenile hackers to cybercriminal enterprises as a existential danger. Governments and private organizations should put in place holistic programs to redirect juveniles away from cybercrime, the CSRB found in its analysis of the success of the Lapsus$ group in attacking "some of the world's most well-resourced and well-defended companies."
Yet young programmers and technology-savvy teenagers often find other ways into the cybercriminal fold as well, says Critical Start's Jones.
"Hackers, like any population group, are diverse individuals with varied motivations, skills, and approaches," she says. "While some hackers may start out with game hacks and move to more serious tools and techniques, we often find that cybercriminals tend to target industries and countries with weaker cyber defenses."
 11 months ago
70
11 months ago
70