Web performance and security firm Cloudflare recently mitigated another record-breaking DDoS attack.
According to Matthew Prince, the company’s CEO, the attack peaked at 3.8 terabits per second (Tbps) and 2.14 billion packets per second (Pps). The attack was aimed at an unidentified customer of an unnamed hosting provider that uses Cloudflare services.
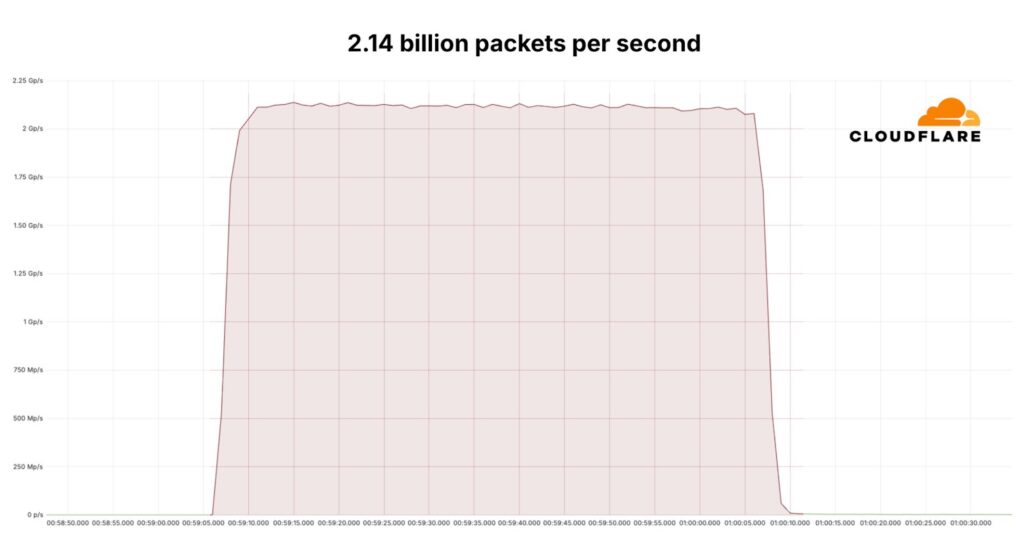
To put the numbers into context, the previous volumetric DDoS record was set in late 2021, when Microsoft saw an attack that peaked at 3.47 Tbps and a packet rate of 340 million Pps. The biggest attack previously seen by Cloudflare peaked at 2.6 Tbps.
In terms of just network protocol attacks, cloud provider OVHcloud in July 2024 reported seeing a record-breaking attack peaking at 840 million Pps.
In terms of application layer DDoS attacks, HTTP/2 Rapid Reset holds the record, with the method being used to launch an attack that peaked at 398 million requests per second (Rps), according to Google’s measurements. The record previously stood at 71 million Rps.
Cloudflare and AWS also saw HTTP/2 Rapid Reset attacks roughly at the same time as Google, but the ones they observed peaked at only 201 million Rps and 155 million Rps, respectively.
In a blog post published on Tuesday morning, Cloudflare revealed that the record-breaking attack was part of a month-long campaign that began in early September. The company has mitigated over 100 of these “hyper-volumetric L3/4 DDoS attacks”, with many of them exceeding 2 billion Pps and 3 Tbps.
The campaign targeted customers in the financial services, telecoms, and internet sectors. The attacks came from systems around the world, including in Vietnam, Russia, Brazil, Spain and the United States, and they were powered by compromised web servers, DVRs, and routers.
*updated with information from CloudFlare blog post
Advertisement. Scroll to continue reading.
Related: Cloudflare Users Exposed to Attacks Launched From Within Cloudflare
Related: After Code Execution, Researchers Show How CUPS Can Be Abused for DDoS Attacks
 4 months ago
27
4 months ago
27