$1.1 billion dollars.
That’s how much ransomware victims paid hackers to unlock their data in 2023. And while $1.1 billion is a staggering sum, it represents only the amount of money that companies and individuals have publicly disclosed.
Ransomware isn’t a new issue for businesses, but despite increased security spending, hackers are emboldened and attacks are on the rise. Here are a few more eye-watering stats:
- Ransomware dwell time decreased to just 24 hours. (Cybermagazine)
- 48% of ransomware victims in the last 12 months suffered reputational damage and lost customers. (Delinea)
- 2024 has seen a 180% increase in the exploitation of vulnerabilities for initial access. (2024 Verizon DBIR)
- There’s been a 68% year-over-year increase in breaches resulting from a third party, and that’s mainly due to software vulnerabilities exploited in ransomware and extortion attacks. (2024 Verizon DBIR)
Security teams are struggling to proactively identify attacks in the early stages, and teams often lack visibility into ransomware exposures across their entire ecosystem — people, vendors, suppliers, and more. That’s why on the main stage at Predict 2024, Recorded Future is excited to announce enhanced capabilities in the Ransomware Mitigation solution and workflow within our Threat Intelligence Module.

Learn more about our powerful ransomware mitigation capabilities
Supporting Our Clients in the Fight Against Ransomware
Recorded Future’s Ransomware Mitigation offering has always encompassed Threat Intelligence, Identity Intelligence, and Attack Surface intelligence. It’s made up of the following components:
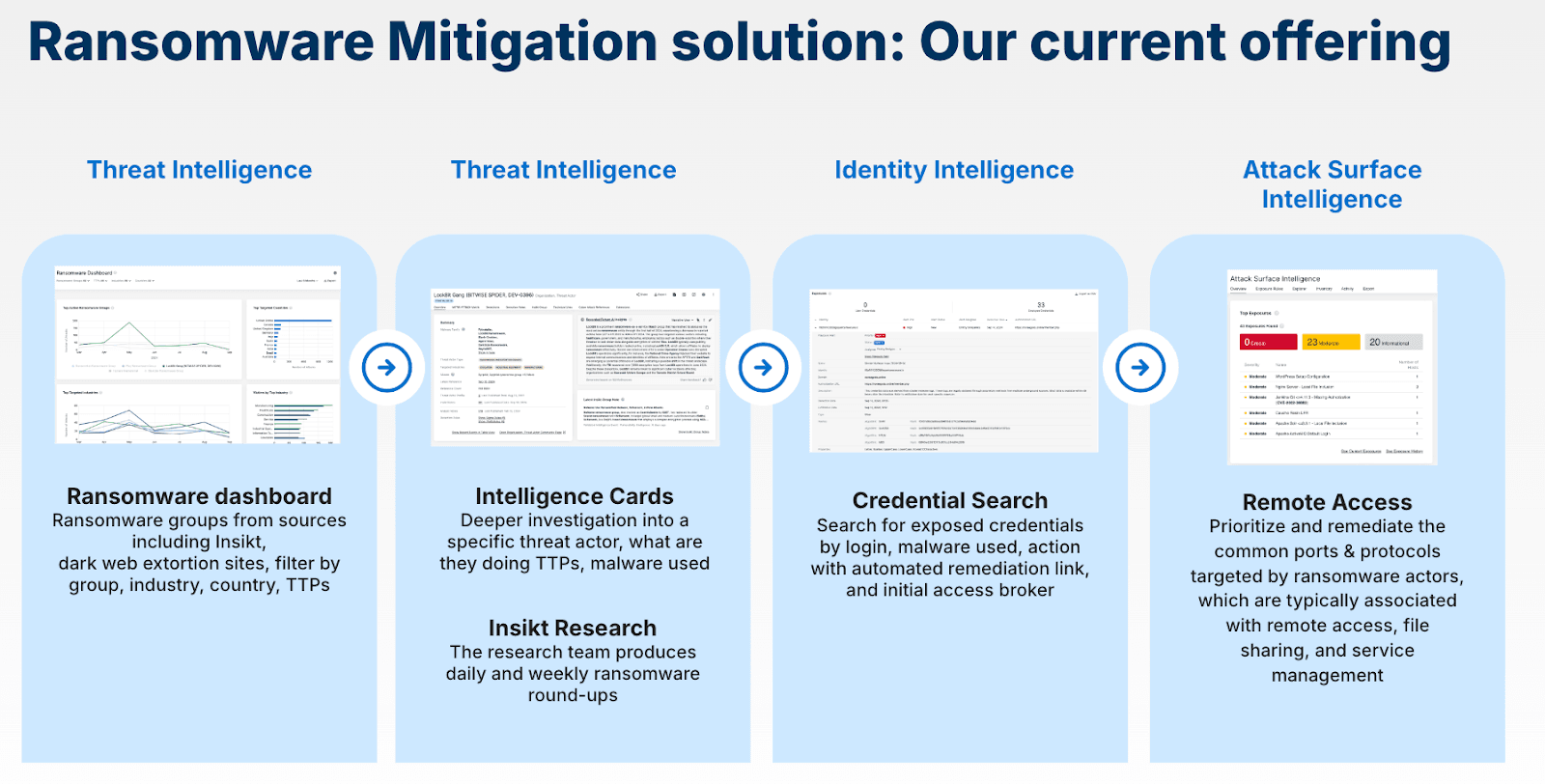
- Threat Intelligence | Ransomware Dashboard and Intelligence Cards. This Dashboard displays threat information from our Insikt Group as well as dark web extortion sites, allowing clients to filter by ransomware group, industry, country, and TTPs to find relevant threats. Intelligence Cards ™ provide a deeper look into specific threat actors and the malware they’re deploying.
- Identity Intelligence | Credential Search Capabilities. Clients can search for exposed credentials by login details, malware used, and initial access brokers — and instantly trigger automated remediation workflows with a single click.
- Attack Surface Intelligence | Remote Access Detection. Clients can prioritize and remediate the common ports and protocols targeted by ransomware actors, which are typically associated with remote access, file sharing, and service management.
Based on what we’ve seen in our work with over 2,000 of global clients, we’ve developed three new advanced capabilities in our Ransomware Mitigation solution to help security teams proactively address threats.
“While proactive defense and resilience to ransomware attacks are achievable with the right intelligence, an AI-driven approach puts security teams ahead of their adversaries' next move,” said Dr. Christopher Ahlberg, Co-founder and CEO, Recorded Future. We’ve looked at the ransomware lifecycle and applied Recorded Future AI, combined with our threat intelligence and client telemetry, to create a single source of truth, defeating ransomware early for each one of our clients.”
Ultimately, these new capabilities empower security teams to prepare for ransomware attacks proactively, detect them early, and act quickly post-attack to avoid harm to their finances, operations, and reputations. Here’s why it’s never been easier for security teams to operationalize and streamline the work of ransomware detection

Discover the latest ransomware defense updates to the Threat Intelligence module
#1: When Time is of the Essence, Detect Threats Faster with Our New
Ransomware Risk Profile
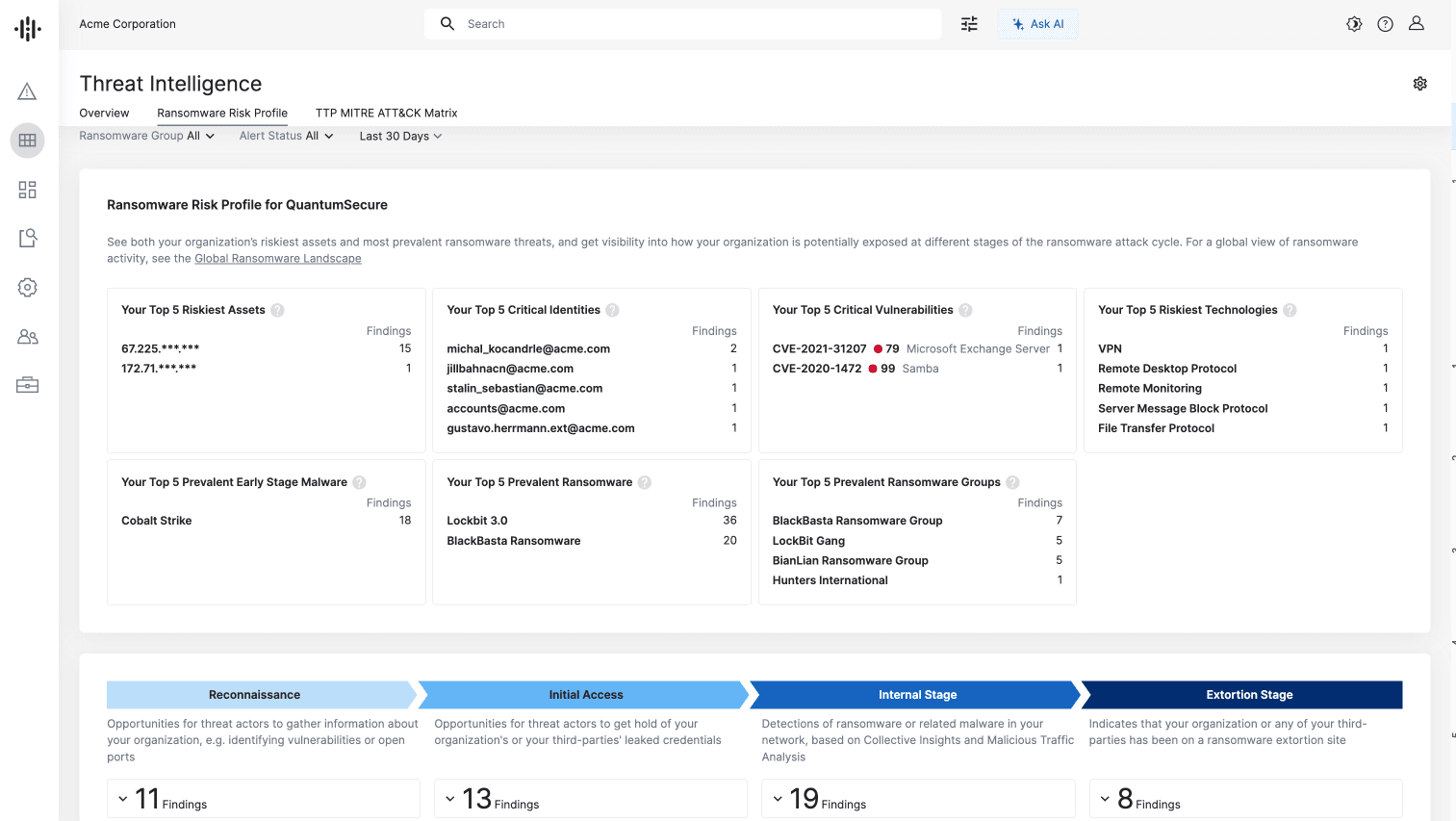
While other solutions on the market focus on the final stages of ransomware threat detection, Recorded Future can help detect threats long before they become issues. The new Ransomware Risk Profile provides an end-to-end view of an organization’s ransomware exposure across the attack lifecycle as well as guidance for each identified threat. This ensures that clients can better identify risks early, prioritize action, and take targeted mitigation steps before attackers can exploit vulnerabilities.
Key features allow clients to:
Review their riskiest assets, top ransomware-related CVEs, critical leaked identities, and top malwares and threat actors specific to the organization.
Tap into expert guidance for each identified threat (e.g, exploited software) with recommended actions that include patch and remediation instructions as well as threat hunting packages created by Insikt Group.
Detect potential compromises before data exfiltration occurs with intelligence provided by Collective Insights.
Gain a clear view of ransomware-specific ports, services, vulnerabilities, and admin pages that can be leveraged by threat actors with ransomware identification and tagging in the Attack Surface Intelligence module. Quickly block entry points and exposures used by ransomware groups.
Identify ransomware threats and early-stage malware impacting the organization with Network Intelligence, which tracks malicious activity across malware families and related infrastructure globally.
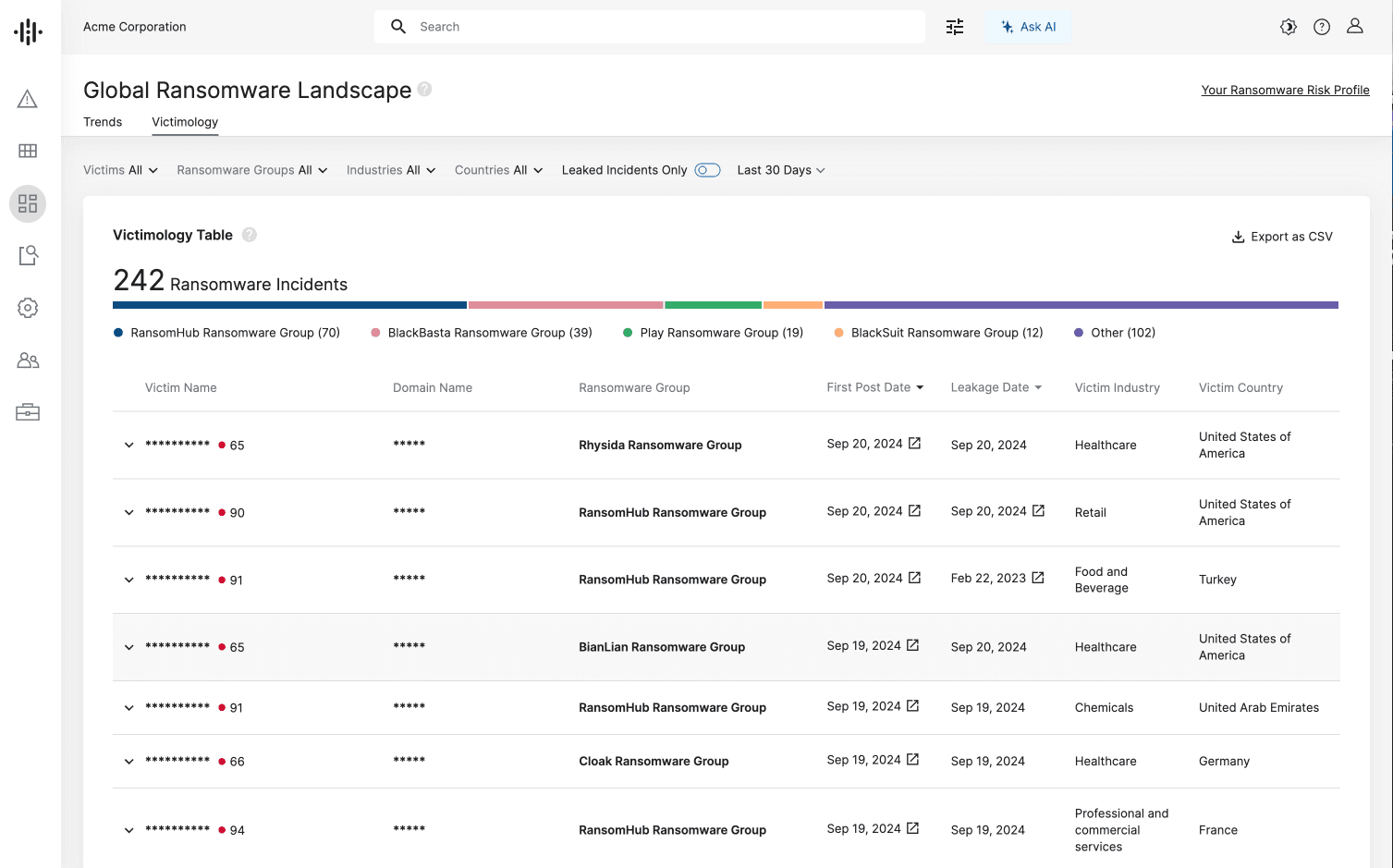
#2: Get Granular Details From Our New Victimology Table and Ransomware Actor Insights
Our new Victimology table and updated Intelligence Cards™ deliver real-time visibility into ransomware victims in an organization’s ecosystem, including industry, geography, and supply chain; detailed threat actor breakdowns; and secure dark web browsing to help security teams proactively defend the organization without endangering its risk posture.
These new insights enable teams to:
Safely browse dark web ransomware extortion websites and search for files containing API “secrets” — all without the need to visit these potentially malicious sites.
Identify leaked data like secrets, regulated information, and IP from companies in the supply chain that have been breached.
Gain visibility into ransomware group operations through precise MITRE ATT&CK mappings, linking specific vulnerabilities, files, and products to each TTP for highly targeted defense planning.
Leverage the latest research on top ransomware groups in updated Intelligence Cards™ provided by Insikt Group. For example, get details on the Rhysida hacker group and identify any relevant vulnerabilities.
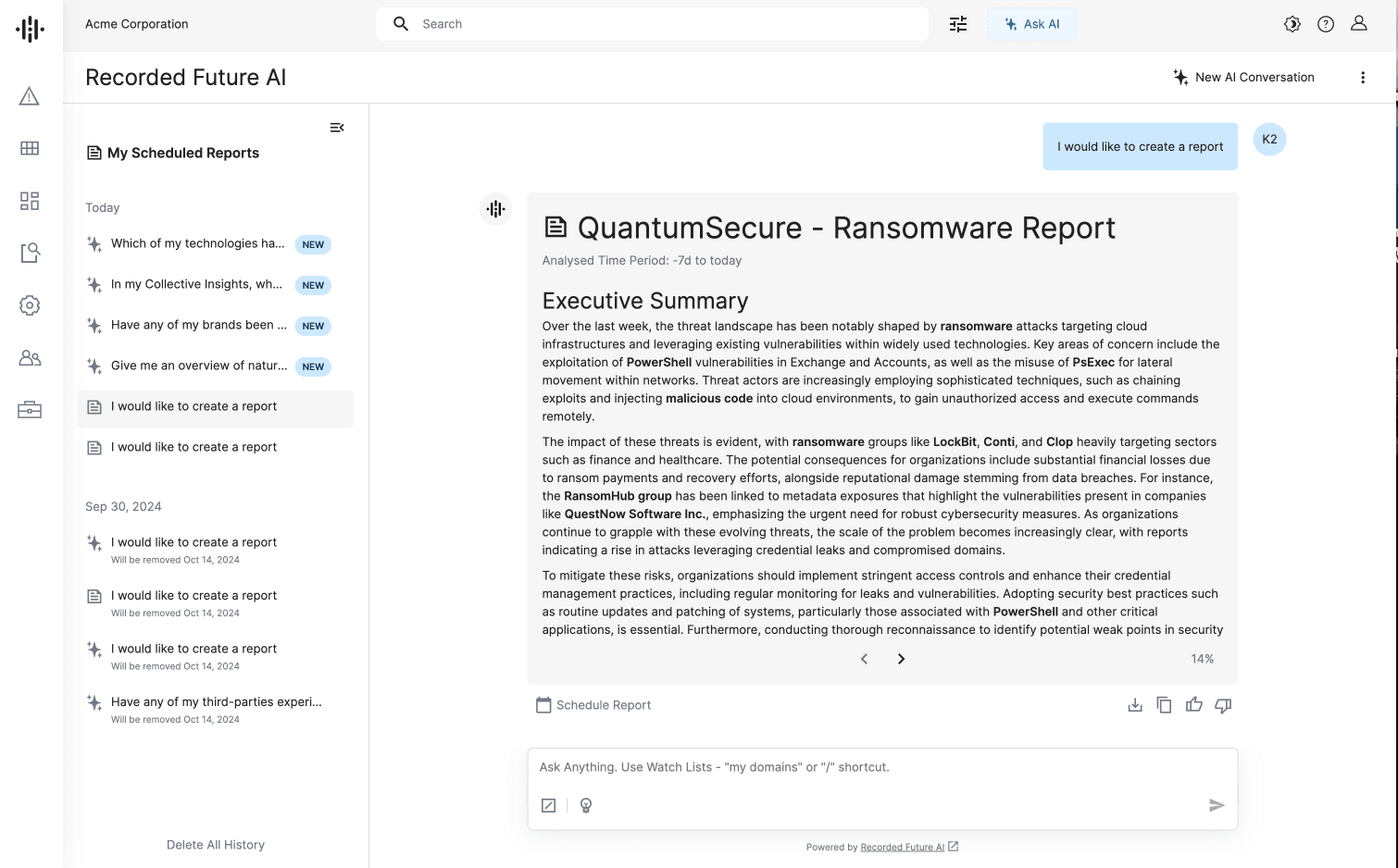
#3: Get Custom Reports with AI Reporting for Ransomware
Now security teams can keep their leadership and organization up to date with the most relevant and timely ransomware intelligence through automated, AI-driven reporting. Recorded Future AI combines knowledge about your company with our Intelligence Graph® to produce actionable, organization-specific insights.
Our new capabilities enable clients to:
Automatically generate customized, audience-specific ransomware intelligence reports, reducing manual effort and saving time.
Generate tailored insights, with sources including telemetry from Collective Insights and the organization’s IT stack from its watchlists.
Get reliable results from Recorded Future AI, which is built on our Intelligence Graph® and which automatically collects data across adversaries, their infrastructure, and organizations they target from proprietary sources. Results are always tagged to the original source for transparency and trust in AI.
Get Ahead of Ransomware Attacks
By leveraging Recorded Future’s new Threat Intelligence capabilities, clients can take a proactive stance to combating ransomware actors. As Jeremy Miller, Cyber Threat Intelligence Analyst at Nelnet, puts it: “With Recorded Future’s Threat Intelligence module we will be able to produce reports using AI Reporting with actionable insights on the highest priority threats to inform stakeholders across the organization. This will help us know how to best protect our organization, and increases our resilience."
For more information about the new capabilities or to see them in action, reach out to request a demo or sign-up to watch the Predict on demand.