
Source: Romolo Tavani via Shuttertock
A data-focused approach to tackling phishing and business fraud promises significant reductions in the amount of phishing and phone-based fraud that companies — and their customers — face, but worries remain over whether fraudsters will adapt.
The Financial Services Information Sharing and Analysis Center (FS-ISAC) unveiled its Phishing Prevention Framework on Nov. 19, a program consisting of best practices in data collection, defense, and customer communications that has already reduced the volume of phishing incidents — as measured by abuse complaints — in a pilot program with three banks. The framework cut the incidence of abuse complaints for those financial services firms in half and promises significant benefits for any business targeted by cybercriminals, if they implement certain best practices — such as security education and intelligence collection — included in the framework.
While FS-ISAC has released the framework for the financial services sector — where phishing is a pernicious problem — the techniques are broadly applicable, says Linda Betz, executive vice president of global community engagement at the organization.
"While the framework is tailored for financial institutions due to the sensitive nature of their operations, the strategies can benefit businesses across industries," she says. "For instance, cataloging communication channels and deploying anti-phishing technologies are broadly applicable and scalable solutions for any organization dealing with sensitive customer interactions or high volumes of transactional data."
The financial services sector is not the only industry plagued by phishing. In 2023, US consumers and businesses reported nearly 300,000 phishing-related crimes to the FBI, according to its annual Internet Crime Report. Phishing and pretexting — which differ in that the attacker surreptitiously joins an email thread — account for 31% and 40%, respectively, of all social engineering attacks, according to Verizon's "2024 Data Breach Investigations Report" (DBIR). Security awareness exercises have found that it takes less than 60 seconds for the first victims of a phishing campaign to click a link and enter their information.
Focus on Sources, Not Transactions
As part of its Phishing Prevention Framework, the FS-ISAC recommends that organizations create a data-focused process for handling abuse complaints and focus on maximizing the insights that can be learned from phishing campaigns. Companies should create a fraud and phishing intake pipeline that records critical information and an abuse box infrastructure that allows security and fraud teams to disseminate intelligence to other business groups, the report states.
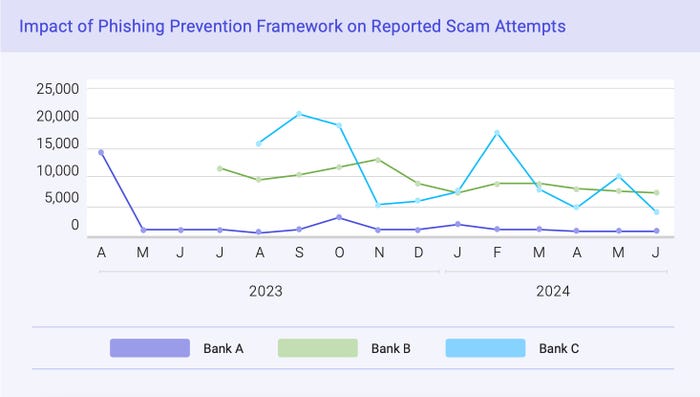
Three banks that piloted the Phishing Prevention Framework all saw decreases in phishing abuse, but Bank A saw the most dramatic changes. Source: FS-ISAC's "Stop the Scams: A Phishing Prevention Framework for Financial Services" report
The key issue is that fraud reporting often focuses on preventing the bad transaction and spends little time on understanding how the activity originated, FS-ISAC's Betz says.
"Structuring the abuse box to glean that information from the customer helps the financial institution know where to focus to address the root cause and take actions to reduce the risk and prevent future attempts, then share the actionable intelligence across the organization and the sector," she says. "[Companies] should implement structured fraud reporting systems to capture actionable data, coordinate across relevant departments, and participate in industrywide threat intelligence platforms to help the entire sector understand the current tactics being used by fraudsters."
The framework also calls for cataloging all of the ways a business communicates with customers and partners, a potentially time-consuming process. While automation can help, collaborating internally across groups and with third parties is key, says Betz.
"Leveraging a succinct data collection survey including the type, origin, and results of the fraudulent activity can help establish any trends in the phishing attempts and better identify any weak areas within networks," she says.
Keeping Up With Attackers
While all the steps included in the framework are common sense approaches to anti-phishing, implementing them all will take time, says Betz. For that reason, the FS-ISAC has listed the actions along with a step number to prioritize defensive efforts.
Whether establishing the processes and technologies called for by the Phishing Prevention Framework will lead to fewer successful phishing campaigns or just force attackers to evolve remains to be seen, says Matthew Harris, senior product manager for fraud at OpSec Security, a brand protection and anti-fraud firm.
"One thing I've learned about dealing with fraudsters is that they'll pivot instantly, and the problem is that they'll pivot far faster than any other company can pivot," he says. "If they realize that there's a way that they can get better ROI, they'll do it."
Scammers are already moving toward phishing attacks that increasingly use voice calls. Phone-based phishing started as a minor issue in 2021 and now accounts for nearly a quarter (23%) of all phishing attacks, according to data collected by OpSec Security. Phone-based phishing includes SMS phishing — "smishing" — and phishing emails that include a fraudulent phone number.
Because there are fewer integrity checks on phone calls, cyberattackers will likely increasingly use the telecommunications channel in their scams, says OpSec's Harris.
"As email security ... has gotten more and more advanced, it becomes more and more difficult [for a scammer] to communicate a traditional email to a person," he says. "By pivoting away from email and toward a phone number, ... there's a good chance a person is going to pick up that phone [giving them] access to the victim directly."
For that reason, the final step of the FS-ISAC's framework includes collaborating with telecommunications firms to reduce the attack surface area through phone systems. Many providers have technologies or services, such as "Do Not Originate," on numbers that are inbound only, giving business customers additional controls, says FS-ISAC's Betz.
"Partnerships with telecommunications providers are increasingly collaborative, as these companies recognize the mutual benefits of reducing spam and phishing attacks," she says.
 2 months ago
32
2 months ago
32