
Complex syslog ecosystems can be challenging
Monitoring devices and applications that provide output via the syslog protocol is a must-have for many organizations. The key to success is making data in this complex ecosystem actionable, as many types of syslog producers exist. These include traditional on-premises network devices and servers for infrastructure applications like databases, websites, or email. You also might be required to capture syslog messages from cloud services on AWS, Azure, and Google Cloud related to resource provisioning, scaling, and security events.
Syslog’s unique nature is also often a challenge. While newer syslog daemons have implemented support for TLS encryption, you can still encounter unauthenticated and plain-text message exchanges. A local endpoint in a protected network or DMZ is required to capture these messages.
Finally, adding additional components on the edge to filter and transform syslog messages (for example, Dynatrace OpenTelemetry distribution) isn’t always possible due to architectural reasons or because it adds unnecessary complexity and cost of ownership when scaling your business.
The ultimate challenge lies in making data from syslog-supported log sources actionable. Without seeing syslog data in the context of your infrastructure, metrics, and transaction traces, you’re slowed down by manual work with siloed data. Without syslog in your observability platform, you miss out on automation, insight into service level objectives, faster mean time to repair, increased security, and resiliency.
Secure and trusted local endpoint now collects syslog data
Dynatrace now makes integrating syslog data into an AI-powered observability platform for cloud and hybrid deployments easy, simple, and secure. After ingesting syslog data safely via Environment ActiveGate, you automatically make it actionable in the right context of your infrastructure and cloud services. At the same time, you can offload the overhead and component upkeep burden to a known and trusted observability platform.
With Davis® AI automatic detection of problems and degradations in your services, you can use syslog data automatically in the context of the correct infrastructure component to fix problems faster with logs and eliminate manual correlation and guesswork. This speeds up your teams’ mean time to identify (MTTI) issues and repair (MTTR), increasing business resiliency to disruptions.
One change to send syslog to Dynatrace
You can now use the syslog ingestion endpoint on Dynatrace Environment ActiveGate for performant network and system monitoring. ActiveGate establishes Dynatrace presence in your local network and serves as a known, trusted, supported technology component with lifecycle management that greatly reduces your maintenance effort. ActiveGate also optimizes traffic volume in your network and serves as a secure relay layer in protected networks and DMZs.
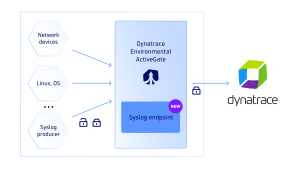
To enable syslog collection on an ActiveGate host, one change to extensionsuser.conf is required. No restart is necessary, and the endpoint is ready on standard ports (514 for UDP and 601 for TCP) to collect and forward logs to Dynatrace.
Change this setting in the ActivateGate extensionsuser.conf file:
#Syslog configuration Syslogenabled=trueTo complete the integration, you need to configure your syslog producer to send data to the Environment ActiveGate IP and port.
Optionally, you can adjust syslog collection beyond the default ports and configuration settings. For example, you might want to enable and provide a certificate for the TLS protocol for secure message exchange. ActiveGate uses an embedded Dynatrace OpenTelemetry Collector instance, which allows you to configure a syslog receiver according to your needs.
What’s next
See these related resources for complete details about Dynatrace syslog support:
- Syslog ingestion is available with Dynatrace Environment ActiveGate version 1.295.
- Read syslog ingestion documentation with configuration samples.
- Setting up your first Environment ActiveGate? See installation documentation for setup.
- For alternative syslog monitoring scenarios, explore syslog (via OpenTelemetry Collector) and syslog (via Fluentd) in Dynatrace Hub.
Coming soon
- We continue to improve syslog integration with easier failover configuration and support for monitoring configuration health.
- Need to send syslog directly over HTTPS? More mature syslog producers support this, and we continue working on providing the required authentication layer.
The post Observe syslog with Dynatrace ActiveGate, a secure, trusted edge component appeared first on Dynatrace news.
 7 months ago
73
7 months ago
73