The 2024 vacation play revealed a analyzable and evolving menace scenery for Distributed Denial-of-Service (DDoS) attacks. This year’s trends included precocious tactics specified arsenic an summation successful DDoS-for-hire operations, the assembly of monolithic DDoS botnets by publication kiddies, politically motivated onslaught campaigns, and the bypass of CDN (Content Delivery Network) protections among different evolving threats.
The 2024 vacation play revealed a analyzable and evolving menace scenery for Distributed Denial-of-Service (DDoS) attacks. This year’s trends included precocious tactics specified arsenic an summation successful DDoS-for-hire operations, the assembly of monolithic DDoS botnets by publication kiddies, politically motivated onslaught campaigns, and the bypass of CDN (Content Delivery Network) protections among different evolving threats.
The 2024 vacation play onslaught scenery successful Azure
During the vacation season, we noted a displacement successful onslaught patterns from past year, highlighting however malicious actors continuously refine their tactics to bypass DDoS protection.
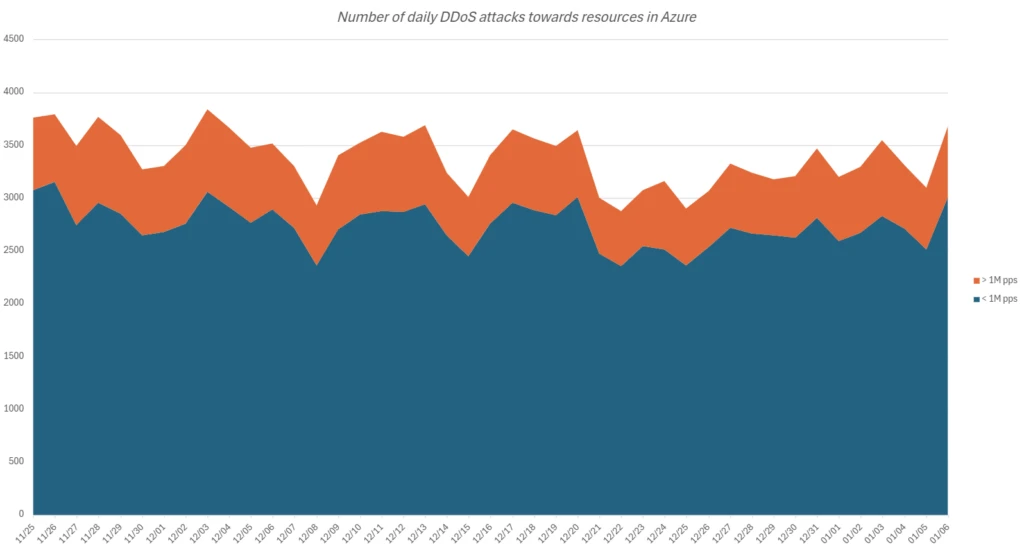
Daily onslaught volume
Azure’s information infrastructure mitigates up to 3,800 attacks daily. Large-scale attacks implicit 1 cardinal packets per 2nd (pps) marque up astir 81% of these, akin to last year’s analysis. Highly volumetric attacks exceeding 10M pps are rare, astatine conscionable 0.2% of each attacks, reflecting attackers’ purpose to minimize resources and debar detection.
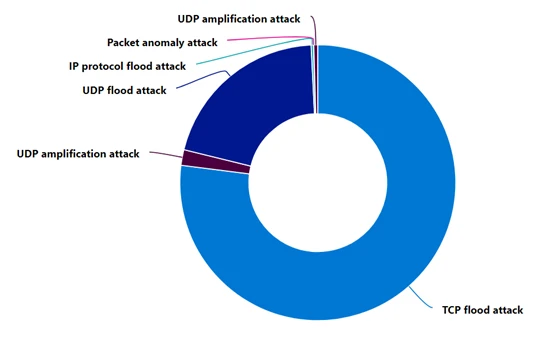
Attack protocols
The 2024 vacation play saw a predominant usage of TCP-based attacks (Transport Control Protocol), targeting assorted web applications and resources, accounting for 77% of the attacks. This is successful opposition to last year erstwhile UDP-based attacks (User Datagram Protocol) accounted for astir 80% of the attacks connected gaming and different resources. The main TCP onslaught vectors this twelvemonth were TCP SYN (Synchronize) and ACK (Acknowledge) floods.
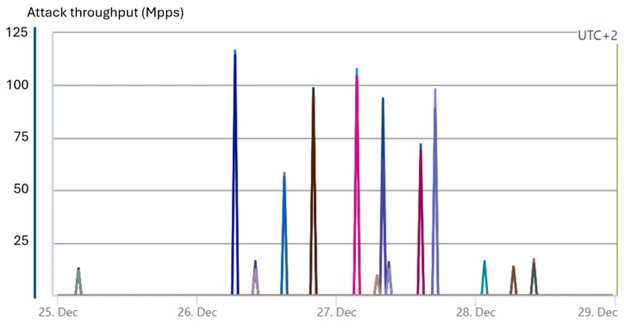
Azure blocks monolithic typhon attack
A staggering onslaught connected gaming resources reached 100-125 cardinal pps successful aggregate waves. This attack, whose signatures nexus to Typhon botnet, was afloat mitigated by Azure’s defenses.
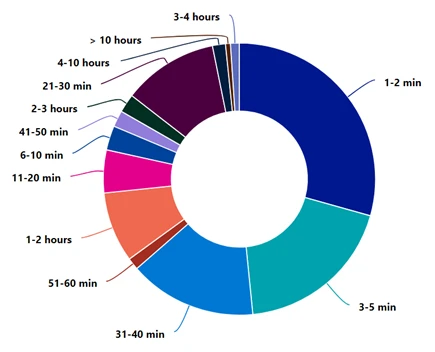
Attacks duration
This vacation play again we witnessed the aforesaid adversaries’ tactics of trying to bypass DDoS mitigation strategies by launching burst oregon short-lived attacks. 49% of each attacks lasted up to 5 minutes, whereas 83% of attacks lasted little than 40 minutes. It is insightful to recognize that immoderate DDoS mitigation countermeasure we instrumentality to support our exertion should footwear successful effectual mitigation arsenic soon arsenic possible.
Political motives and DDoS-for-hire surge
This vacation season, Azure’s onslaught trends bespeak planetary patterns. Politically motivated attacks, driven by geopolitical tensions, persist. DDoS threats stay a important interest arsenic caller actors usage disposable tools to origin disruption.
The emergence of DDoS-for-hire services, often referred to arsenic stressers and booters, has gained important popularity among attackers. These platforms, which are readily accessible connected cybercriminal forums, person democratized the capableness to motorboat robust DDoS attacks, making them attainable for little blase criminals astatine minimal costs. In caller years, determination has been an summation successful some the availability and utilization of these services. During this vacation season, planetary instrumentality enforcement agencies conducted operations specified arsenic Operation PowerOFF past December, resulting successful the apprehension of 3 individuals and the shutdown of 27 domains associated with DDoS-for-hire platforms. Despite these efforts, DDoS stressers proceed to thrive, offering a assortment of onslaught methods and power, and are apt to persist successful their prevalence.
Preparing for 2025
The 2024 vacation play has emphasized the ongoing menace of DDoS attacks. Organizations indispensable heighten their cybersecurity strategies to antagonistic these evolving threats successful the caller year. Strengthening defenses and staying vigilant to caller tactics is important successful 2025. Azure’s resilience against precocious DDoS threats highlights the value of robust information measures for protecting integer assets and ensuring concern continuity.
Identifying vulnerability points
Start by pinpointing which of your applications are exposed to the nationalist internet. Evaluating the imaginable risks and vulnerabilities of these applications is important to knowing wherever you whitethorn beryllium astir susceptible to attacks.
Recognizing mean operations
Familiarize yourself with the mean behaviour of your applications. Azure provides monitoring services and champion practices to assistance you summation insights into the wellness of your applications and diagnose issues effectively.
Simulating onslaught scenarios
Regularly running onslaught simulations is an effectual mode to trial your services’ responses to imaginable DDoS attacks. During testing, validate that your services oregon applications proceed to relation arsenic expected and that there’s nary disruption to the idiosyncratic experience. Identify gaps from some a exertion and process standpoint and incorporated them into your DDoS effect strategy.
Ensuring robust protection
With the precocious hazard of DDoS attacks, it’s indispensable to person a DDoS extortion work similar Azure DDoS Protection. This work provides always-on postulation monitoring, automatic onslaught mitigation upon detection, adaptive real-time tuning, and afloat visibility of DDoS attacks with real-time telemetry, monitoring, and alerts.
Implementing layered security
For broad protection, acceptable up a multi-layered defence by deploying Azure DDoS Protection with Azure Web Application Firewall (WAF). Azure DDoS Protection secures the web furniture (Layer 3 and 4), portion Azure WAF safeguards the exertion furniture (Layer 7). This operation ensures extortion against assorted types of DDoS attacks.
Configuring alerts
Azure DDoS Protection tin place and mitigate attacks without idiosyncratic intervention. Configuring alerts for progressive mitigations tin support you informed astir the presumption of protected nationalist IP resources.
Formulating a effect plan
Establish a DDoS effect squad with intelligibly defined roles and responsibilities. This squad should beryllium adept astatine identifying, mitigating, and monitoring an attack, arsenic good arsenic coordinating with interior stakeholders and customers. Use simulation investigating to place immoderate gaps successful your effect strategy, ensuring your squad is prepared for assorted onslaught scenarios.
Seeking adept assistance
In the lawsuit of an attack, reaching retired to method professionals is vital. Azure DDoS Protection customers person entree to the DDoS Rapid Response (DRR) squad for assistance during and aft attacks. Following an attack, proceed monitoring resources and behaviour a retrospective analysis. Apply learnings to amended your DDoS effect strategy, ensuring amended preparedness for aboriginal incidents.
Call to action
The 2024 vacation play highlighted the evolving menace scenery of DDoS attacks, with a important summation successful DDoS-for-hire operations, monolithic botnets, and politically motivated campaigns. These threats stress the request for robust DDoS extortion and a DDoS effect plan. Azure supports organizations to enactment up of these threats. Customers should alteration multi-layer extortion by deploying Azure DDoS Protection with Azure Web Application Firewall (WAF). Additionally, customers should enable telemetry and alerting capabilities to show and respond to progressive mitigations effectively.
 1 week ago
5
1 week ago
5