Law enforcement on Tuesday used the previously seized websites of the LockBit ransomware group to announce more arrests and infrastructure disruptions.
Europol, the UK and the US have all issued press releases in addition to the announcements made on the former LockBit sites. Europol announced new law enforcement actions, including the arrest of an alleged LockBit developer at the request of France while he was vacationing outside of Russia, and the arrests of two individuals in the UK for supporting the activity of a LockBit affiliate.
In Spain, police arrested the alleged administrator of a bulletproof hosting service, which enabled authorities to seize nine servers that were part of LockBit infrastructure. The suspect, authorities say, “was one of the main facilitators of infrastructure for LockBit”, and the information they obtained will be useful for prosecuting core members and affiliates of the cybercrime enterprise.
The most important announcement, however, is related to the unmasking of a Russian national, Aleksandr Viktorovich Ryzhenkov, 31, who authorities say is not only a LockBit affiliate, but also a member of Evil Corp, the infamous profit-driven cybercrime organization that may have also run cyberespionage operations on behalf of the Russian government.
“Ryzhenkov used the affiliate name Beverley, made over 60 LockBit ransomware builds and sought to extort at least $100 million from victims in ransom demands. Ryzhenkov additionally has been linked to the alias mx1r and associated with UNC2165 (an evolution of Evil Corp affiliated actors),” authorities said.
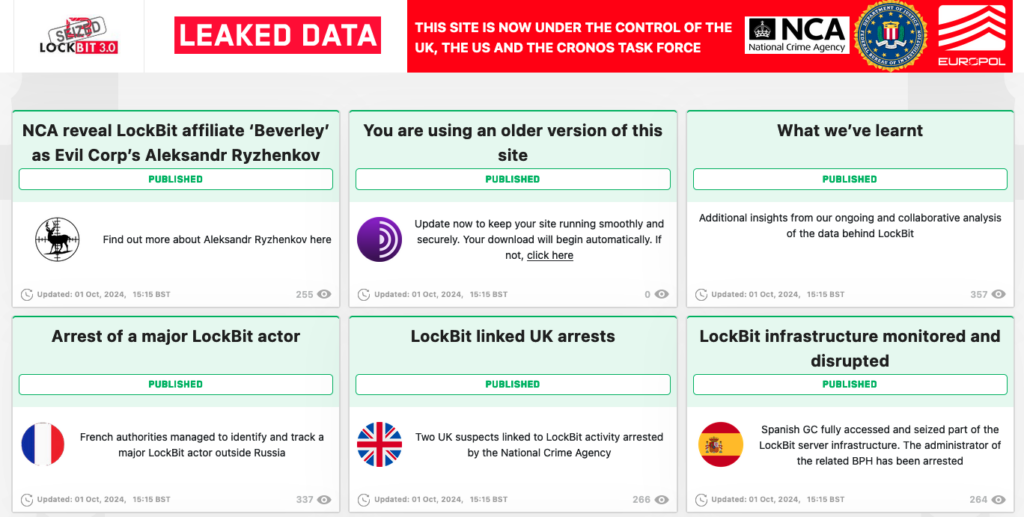
The US Justice Department on Tuesday announced charges against Ryzhenkov, but not for LockBit attacks. Instead, he has been charged over BitPaymer ransomware attacks.
Ryzhenkov is one of the 16 alleged Evil Corp members that were sanctioned on Tuesday by the US, UK, and Australia. The sanctions also target Maksim Yakubets, who is said to be the leader of Evil Corp and who has a $5 million bounty on his head. Authorities say Ryzhenkov is Yakubets’ right-hand man.
According to government agencies, the LockBit operation hit over 2,500 entities across more than 120 countries.
Advertisement. Scroll to continue reading.
Law enforcement agencies from the US, UK and several other countries announced in February 2024 that the LockBit ransomware had been severely disrupted as part of Operation Cronos, an operation that involved server seizures and arrests.
The Tor domains used at the time by the LockBit gang to name victims and leak stolen information were taken over by the UK’s National Crime Agency (NCA) and used to make announcements related to the operation.
In early May, law enforcement announced that it had discovered the real identity of the mastermind behind the cybercrime operation. Investigators determined that Dimitry Yuryevich Khoroshev of Voronezh, Russia, is the LockBit administrator known online as LockBitSupp, and the US Justice Department announced charges against him.
Khoroshev has been accused of creating and operating LockBit and allegedly receiving over $100 million of the more than $500 million received by affiliates from victims. A reward of up to $10 million has been offered for information on Khoroshev.
Two LockBit affiliates have since been charged and pleaded guilty in the United States.
Despite the actions taken by law enforcement, LockBit had apparently not stopped conducting attacks, immediately creating new leak websites and continuing to target organizations.
In fact, in May LockBit once again became the most active ransomware operation, although some experts questioned whether it was a real surge in attacks or a smokescreen whose goal was to hide the true state of the criminal enterprise.
Indeed, the number of attacks claimed by LockBit in June, July and August dropped significantly. In June, the cybercriminals announced hacking the US Federal Reserve, but leaked data from a relatively small financial services company. That appears to have been their last major announcement.
When SecurityWeek checked LockBit’s leak websites on September 30, they all appeared to be offline, a fact confirmed by researcher Dominic Alvieri, who has closely monitored ransomware attacks over the past years. However, Alvieri later noticed that, at some point during the day, LockBit’s more recent leak sites came back online, but they do not appear to have been updated since May 29.
One of the posts published by the NCA on the LockBit website on Tuesday, titled ‘The demise of LockBit since February 2024’, reveals that the law enforcement actions against LockBit were successful and the cybercrooks were significantly hit.
“LockBit has lost affiliates, some of whom are likely to have moved to other Ransomware-as-a-Service providers as a result of the Operation Cronos disruption,” the NCA said. “The LockBit Ransomware-as-a-Service group has resorted to duplicating claimed victims, almost certainly to boost victim numbers and mask the impact of Operation Cronos. Of the significant large victims claimed since the takedown, two thirds are complete lies from LockBit (quelle surprise!), and the remaining third cannot be verified as real victims.”
“LockBit’s reputation has been tarnished by the Operation Cronos disruption and their recovery attempts have been undermined as a result. The financial impact of this disruption has not only impacted Dmitry Khoroshev a.k.a. LockBitSupp, but has also deprived associated threat actors of their funds,” the agency added.
Related: Hawaii Health Center Discloses Data Breach After Ransomware Attack
Related: Microsoft: Cloud Environments of US Organizations Targeted in Ransomware Attacks
Related: Hackers Demand $6 Million for Files Stolen From Seattle Airport Operator in Cyberattack
 4 months ago
26
4 months ago
26