New research shows that over 4 million systems on the internet, including VPN servers and home routers, are vulnerable to attacks due to tunneling protocol vulnerabilities.
The research was conducted by Mathy Vanhoef, a professor at the KU Leuven university in Belgium, and PhD student Angelos Beitis, in collaboration with VPN testing company Top10VPN. Vanhoef is well known for his Wi-Fi security research, including for the attacks named Dragonblood, KRACK and FragAttacks.
Tunneling protocols are used to transport data between different networks and are essential to the functioning of the internet because they allow networks to carry communications that they may not support — for instance, running IPv6 over an IPv4 network. They enable this by encapsulating a packet inside another packet.
Building on previous research that showed IPv4 hosts accept unauthenticated IPIP traffic from any source, Vanhoef and Beitis identified several tunneling protocols vulnerable to abuse, including IPIP/IP6IP6, GRE/GRE6, 4in6 and 6in4.
According to the researchers, misconfigured systems accept tunneling packets without checking the sender’s identity. A threat actor can exploit this to send specially crafted packets storing the victim’s IP to a vulnerable host, causing it to forward the inner packet to the victim and paving the way for various types of attacks.
A threat actor can use this method to conduct anonymous attacks, including to abuse hosts as one-way proxies, conducting DoS attacks and DNS spoofing, and gaining access to internal networks and the IoT devices they host.
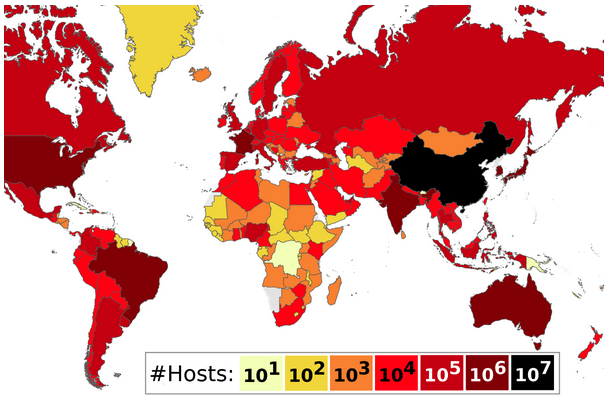
An internet scan conducted by the researchers revealed 4.26 million vulnerable hosts, including VPN servers, home routers provided by ISPs, core internet routers, mobile network gateways and nodes, and CDN nodes. Of these vulnerable hosts, more than 1.8 million are spoofing-capable systems.
“All vulnerable hosts can be hijacked to perform anonymous attacks, as the outer packet headers containing an attacker’s real IP address are stripped. These attacks are easily traceable to the compromised host, however, which can then be secured,” the researchers explained.
Advertisement. Scroll to continue reading.
“Spoofing-capable hosts can have ANY IP address as the source address in the inner packet, so not only does an attacker remain anonymous, but the compromised host also becomes much harder to discover and secure,” they added.
A majority of the vulnerable hosts were discovered in China, followed by France.
The CVE identifiers CVE-2024-7595, CVE-2025-23018, CVE-2025-23019 and CVE-2024-7596 were assigned to these vulnerabilities.
Technical details are available in a blog post published by Top10VPN and an academic paper published by Vanhoef and Beitis. The researchers have also shared defense recommendations that can be implemented by individual hosts and ISPs and other network owners.
Related: Millions of Websites Susceptible to XSS Attack via OAuth Implementation Flaw
Related: Low-Code, High Risk: Millions of Records Exposed via Misconfigured Microsoft Power Pages
Related: Major Backdoor in Millions of RFID Cards Allows Instant Cloning
 2 weeks ago
11
2 weeks ago
11