To say that multi-factor authentication (MFA) is a failure is too extreme. But we cannot say it is successful – that much is empirically obvious. The important question is: Why?
MFA is universally recommended and often required. CISA says, “Adopting MFA is a simple way to protect your organization and can prevent a significant number of account compromise attacks.” NIST SP 800-63-3 requires MFA for systems at Authentication Assurance Levels (AAL) 2 and 3. Executive Order 14028 mandates all US government agencies to implement MFA. PCI DSS requires MFA for accessing cardholder data environments. SOC 2 requires MFA. The UK ICO has stated, “We expect all organizations to take fundamental steps to secure their systems, such as regularly checking for vulnerabilities, implementing multi-factor authentication…”
Yet, despite these recommendations, and even where MFA is implemented, breaches still occur. Why?
Think of MFA as a second, but dynamic, set of keys to the front door of a system. This second set is given only to the identity wishing to enter, and only if that identity is authenticated to enter. It is a different second key delivered for each different entry.
 Jason Soroko, senior fellow at Sectigo.
Jason Soroko, senior fellow at Sectigo.The principle is clear, and MFA should be able to prevent access to inauthentic identities. But this principle also relies on the balance between security and usability. If you increase security you decrease usability, and vice versa. You can have very, very strong security but be left with something equally difficult to use. Since the purpose of security is to enable business profitability, this becomes a conundrum.
Strong security can impinge on profitable operations. This is especially relevant at the point of access – if staff are delayed entry, their work is also delayed. And if MFA is not at maximum strength, even the company’s own staff (who simply want to get on with their work as quickly as possible) will find ways around it.
“Simply put,” says Jason Soroko, senior fellow at Sectigo, “MFA raises the difficulty for a malicious actor, but the bar often isn’t high enough to prevent a successful attack.” Discussing and solving the required balance in using MFA to reliably keep bad guys out while quickly and easily letting good guys in – and to question whether MFA is really needed – is the subject of this article.
The primary problem with any form of authentication is that it authenticates the device being used, not the person attempting access. “It’s often misunderstood,” says Kris Bondi, CEO and co-founder of Mimoto, “that MFA isn’t verifying a person, it’s verifying a device at a point in time. Who is holding that device isn’t guaranteed to be who you expect it to be.”
 Kris Bondi, CEO and co-founder of Mimoto
Kris Bondi, CEO and co-founder of MimotoThe most common MFA method is to deliver a use-once-only code to the entry applicant’s mobile phone. But phones get lost and stolen (physically in the wrong hands), phones get compromised with malware (allowing a bad actor access to the MFA code), and electronic delivery messages get diverted (MitM attacks).
To these technological weaknesses we can add the ongoing criminal arsenal of social engineering attacks, including SIM swapping (persuading the carrier to transfer a phone number to a new device), phishing, and MFA fatigue attacks (triggering a flood of delivered but unexpected MFA notifications until the victim eventually approves one out of frustration). The social engineering threat is likely to increase over the next few years with gen-AI adding a new layer of sophistication, automated scale, and introducing deepfake voice into targeted attacks.
Advertisement. Scroll to continue reading.
These weaknesses apply to all MFA systems that are based on a shared one-time code, which is basically just an additional password. “All shared secrets face the risk of interception or harvesting by an attacker,” says Soroko. “A one-time password generated by an app that has to be typed into an authentication web page is just as vulnerable as a password to key logging or a fake authentication page.”
Learn More at SecurityWeek’s Identity & Zero Trust Strategies Summit
There are more secure methods than simply sharing a secret code with the user’s mobile phone. You can generate the code locally on the device (but this retains the basic problem of authenticating the device rather than the user), or you can use a separate physical key (which can, like the mobile phone, be lost or stolen).
A common approach is to include or require some additional method of tying the MFA device to the individual concerned. The most common method is to have sufficient ‘ownership’ of the device to force the user to prove identity, usually through biometrics, before being able to access it. The most common methods are face or fingerprint identification, but neither are foolproof. Both faces and fingerprints change over time – fingerprints can be scarred or worn to the extent of not working, and facial ID can be spoofed (another issue likely to worsen with deepfake images.
“Yes, MFA works to raise the level of difficulty of attack, but its success depends on the method and context,” adds Soroko. “However, attackers bypass MFA through social engineering, exploiting ‘MFA fatigue’, man-in-the-middle attacks, and technical flaws like SIM swapping or stealing session cookies.”
Implementing strong MFA just adds layer upon layer of complexity required to get it right, and it’s a moot philosophical question whether it is ultimately possible to solve a technological problem by throwing more technology at it (which could in fact introduce new and different problems). It is this complexity that adds a new problem: this security solution is so complex that many companies don’t bother to implement it or do so with only trivial concern.
The history of security demonstrates a continuous leap-frog competition between attackers and defenders. Attackers develop a new attack; defenders develop a defense; attackers learn how to subvert this attack or move on to a different attack; defenders develop… and so on, probably ad infinitum with increasing sophistication and no permanent winner. “MFA has been in use for more than 20 years,” notes Bondi. “As with any tool, the longer it is in existence, the more time bad actors have had to innovate against it. And, frankly, many MFA approaches haven’t evolved much over time.”
Two examples of attacker innovations will demonstrate: AitM with Evilginx; and the 2023 hack of MGM Resorts.
Evilginx
On December 7, 2023, CISA and the UK’s NCSC warned that Star Blizzard (aka Callisto, Coldriver, and BlueCharlie) had been using Evilginx in targeted attacks against academia, defense, governmental organizations, NGOs, think tanks and politicians mainly in the US and UK, but also other NATO countries.
Star Blizzard is a sophisticated Russian group that is “almost certainly subordinate to the Russian Federal Security Service (FSB) Centre 18”. Evilginx is an open source, easily available framework originally developed to assist pentesting and ethical hacking services, but has been widely co-opted by adversaries for malicious purposes.
“Star Blizzard uses the open-source framework EvilGinx in their spear phishing activity, which allows them to harvest credentials and session cookies to successfully bypass the use of two-factor authentication,” warns CISA / NCSC.
On September 19, 2024, Abnormal Security described how an ‘attacker in the middle’ (AitM – a specific type of MitM)) attack works with Evilginx. The attacker starts by setting up a phishing site that mirrors a legitimate site. This can now be easier, better, and faster with gen-AI.
That site can operate as a watering hole waiting for victims, or specific targets can be socially engineered to use it. Let’s say it is a bank ‘site’. The user asks to log in, the message is sent to the bank, and the user gets an MFA code to actually log in (and, of course, the attacker gets the user credentials).
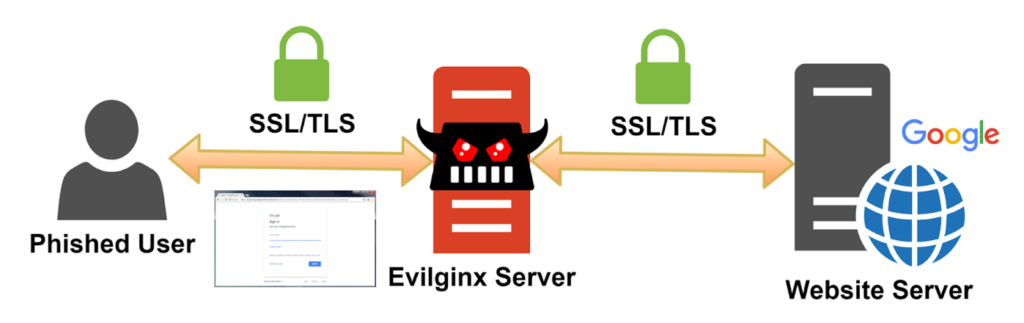
But it’s not the MFA code that Evilginx is after. It is currently acting as a proxy between the bank and the user. “Once authenticated,” says Permiso, “the attacker captures the session cookies and can then use those cookies to impersonate the victim in future interactions with the bank, even after the MFA process has been completed… Once the attacker captures the victim’s credentials and session cookies, they can log into the victim’s account, change security settings, move funds, or steal sensitive data–all without triggering the MFA alerts that would typically warn the user of unauthorized access.”
Successful use of Evilginx negates the one-time nature of an MFA code.
MGM Resorts
In 2023, MGM Resorts was hacked, becoming public knowledge on September 11, 2023. It was breached by Scattered Spider and then ransomed by AlphV (a ransomware-as-a-service organization). Vx-underground, without naming Scattered Spider, describes the ‘breacher’ as a subgroup of AlphV, implying a relationship between the two groups. “This particular subgroup of ALPHV ransomware has established a reputation of being remarkably gifted at social engineering for initial access,” wrote Vx-underground.
The relationship between Scattered Spider and AlphV was more likely one of a customer and supplier: Scattered Spider breached MGM, and then used AlphV RaaS ransomware to further monetize the breach. Our interest here is in Scattered Spider being ‘remarkably gifted in social engineering’; that is, its ability to socially engineer a bypass to MGM Resorts’ MFA.
It is generally thought that the group first acquired MGM staff credentials already available on the dark web. Those credentials, however, would not alone get through the installed MFA. So, the next stage was OSINT on social media. “With additional information collected from a high-value user’s LinkedIn profile,” reported CyberArk on September 22, 2023, “they hoped to dupe the helpdesk into resetting the user’s multi-factor authentication (MFA). They were successful.”
Having dismantled the relevant MFA and using pre-obtained credentials, Scattered Spider had access to MGM Resorts. The rest is history. They created persistence “by configuring an entirely additional Identity Provider (IdP) in the Okta tenant” and “exfiltrated unknown terabytes of data”.
The time came to take the money and run, using AlphV ransomware. “Scattered Spider encrypted several hundred of their ESXi servers, which hosted thousands of VMs supporting hundreds of systems widely used in the hospitality industry.”
In its subsequent SEC 8-K filing, MGM Resorts admitted a negative impact of $100 million and further cost of around $10 million for “technology consulting services, legal fees and expenses of other third party advisors”.
But the important thing to note is that this breach and loss was not caused by an exploited vulnerability, but by social engineers who overcame the MFA and entered through an open front door.
So, given that MFA clearly gets defeated, and given that it only authenticates the device not the user, should we abandon it?
The answer is a resounding ‘No’. The problem is that we misunderstand the purpose and role of MFA. All the recommendations and regulations that insist we must implement MFA have seduced us into believing it is the silver bullet that will protect our security. This simply isn’t realistic.
Consider the concept of crime prevention through environmental design (CPTED). It was championed by criminologist C. Ray Jeffery in the 1970s and used by architects to reduce the likelihood of criminal activity (such as burglary).
Simplified, the theory suggests that a space built with access control, territorial reinforcement, surveillance, continuous maintenance, and activity support will be less subject to criminal activity. It will not stop a determined burglar; but finding it hard to get in and stay hidden, most burglars will simply move to another less well designed and easier target. So, the purpose of CPTED is not to eliminate criminal activity, but to deflect it.
This principle translates to cyber in two ways. Firstly, it recognizes that the primary purpose of cybersecurity is not to eliminate cybercriminal activity, but to make a space too difficult or too costly to pursue. Most criminals will look for somewhere easier to burgle or breach, and – sadly – they will almost certainly find it. But it won’t be you.
Secondly, note that CPTED talks about the complete environment with multiple focuses. Access control: but not just the front door. Surveillance: pentesting might locate a weak rear entry or a broken window, while internal anomaly detection might uncover a burglar already inside. Maintenance: use the latest and best tools, keep systems up to date and patched. Activity support: adequate budgets, good management, proper recompense, and so on.
These are just the basics, and more could be included. But the primary point is that for both physical and cyber CPTED, it is the whole environment that needs to be considered – not just the front door. That front door is important and needs to be protected. But however strong the protection, it won’t defeat the burglar who talks his or her way in, or finds an unlatched, rarely used rear window.
That’s how we should consider MFA: an essential part of security, but only a part. It won’t defeat everyone but will perhaps delay or divert the majority. It is an essential part of cyber CPTED to reinforce the front door with a second lock that requires a second key.
Since the traditional front door username and password no longer delays or diverts attackers (the username is usually the email address and the password is too easily phished, sniffed, shared, or guessed), it is incumbent on us to strengthen the front door authentication and access so this part of our environmental design can play its part in our overall security defense.
The obvious way is to add an additional lock and a one-use key that isn’t created by nor known to the user before its use. This is the approach known as multi-factor authentication. But as we have seen, current implementations are not foolproof. The primary methods are remote key generation sent to a user device (usually via SMS to a mobile device); local app generated code (such as Google Authenticator); and locally held separate key generators (such as Yubikey from Yubico).
Each of these methods solve some, but none solve all, of the threats to MFA. None of them change the fundamental issue of authenticating a device rather than its user, and while some can prevent easy interception, none can withstand persistent, and sophisticated social engineering attacks. Nevertheless, MFA is important: it deflects or diverts all but the most determined attackers.
If one of these attackers succeeds in bypassing or defeating the MFA, they have access to the internal system. The part of environmental design that includes internal surveillance (detecting bad guys) and activity support (assisting the good guys) takes over. Anomaly detection is an existing approach for enterprise networks. Mobile threat detection systems can help prevent bad guys taking over mobile phones and intercepting SMS MFA codes.
Zimperium’s 2024 Mobile Threat Report published on September 25, 2024, notes that 82% of phishing sites specifically target mobile devices, and that unique malware samples increased by 13% over last year. The threat to mobile phones, and therefore any MFA reliant on them is increasing, and will likely worsen as adversarial AI kicks in.
 Kern Smith, VP Americas at Zimperium.
Kern Smith, VP Americas at Zimperium.We should not underestimate the threat coming from AI. It’s not that it will introduce new threats, but it will increase the sophistication and scale of existing threats – which already work – and will reduce the entry barrier for less sophisticated newcomers. “If I wanted to stand up a phishing website,” comments Kern Smith, VP Americas at Zimperium, “historically I would have to learn some coding and do a lot of searching on Google. Now I just go on ChatGPT or one of dozens of similar gen-AI tools, and say, ‘scan me up a website that can capture credentials and do XYZ…’ Without really having any significant coding experience, I can start building an effective MFA attack tool.”
As we’ve seen, MFA will not stop the determined attacker. “You need sensors and alarm systems on the devices,” he continues, “so you can see if anyone is trying to test the boundaries and you can start getting ahead of these bad actors.”
Zimperium’s Mobile Threat Defense detects and blocks phishing URLs, while its malware detection can curtail the malicious activity of dangerous code on the phone.
But it is always worth considering the maintenance element of security environment design. Attackers are always innovating. Defenders must do the same. An example in this approach is the Permiso Universal Identity Graph announced on September 19, 2024. The tool combines identity centric anomaly detection combining more than 1,000 existing rules and on-going machine learning to track all identities across all environments. A sample alert describes: MFA default method downgraded; Weak authentication method registered; Sensitive search query performed… etcetera.
The important takeaway from this discussion is that you cannot rely on MFA to keep your systems safe – but it is an essential part of your overall security environment. Security is not just protecting the front door. It starts there, but must be considered across the whole environment. Security without MFA can no longer be considered security.
Related: Microsoft Announces Mandatory MFA for Azure
Related: Unlocking the Front Door: Phishing Emails Remain a Top Cyber Threat Despite MFA
Related: Cisco Duo Says Hack at Telephony Supplier Exposed MFA SMS Logs
Related: Zero-Day Attacks and Supply Chain Compromises Surge, MFA Remains Underutilized: Rapid7 Report
 3 months ago
42
3 months ago
42