
The report discusses Iranian intelligence and military entities associated with the Islamic Revolutionary Guard Corps (IRGC) involved in cyber activities targeting Western countries through their network of contracting companies. Four known intelligence and military organizations linked to the IRGC engage with cyber contractors. Iranian threat groups linked to the network of contracting parties have launched espionage and ransomware attacks and are leading efforts to destabilize target countries through information operations. The victims are linked to governments, media, non-governmental organizations, critical infrastructure, and the healthcare sector, just to name a few. Some contractors are also implicated in developing technologies that enable surveillance activity that contributes to human rights abuses.
The IRGC-related cyber companies export technologies for surveillance and offensive purposes. The report highlights some select cases of financial activities outside Iran, suggesting contractors likely rely on the IRGC Quds Force (QF) for lucrative arrangements in countries like Iraq, Syria, and Lebanon.
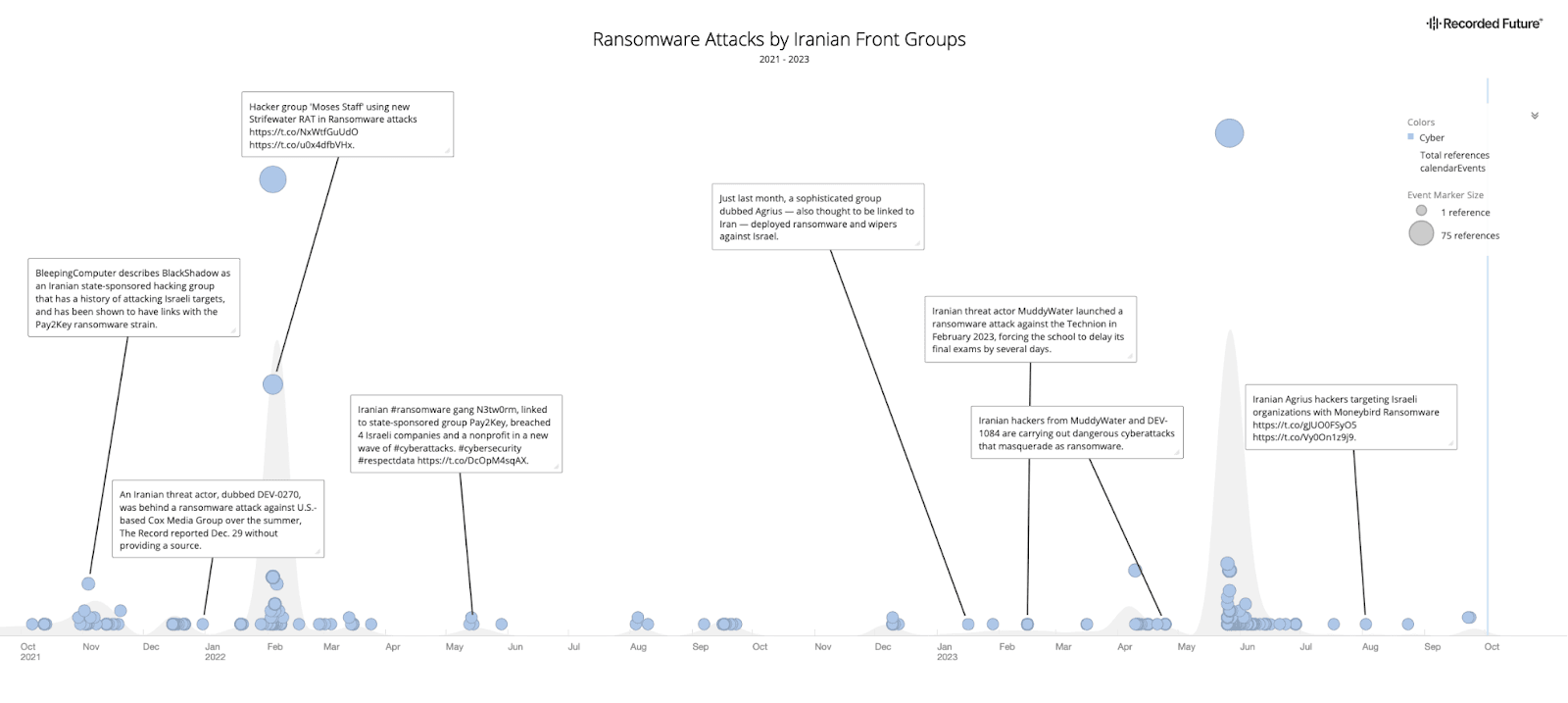 Major ransomware-style attacks led by pro-Iranian government fronts like Moses Staff, N3tW0rm, and Agrius (Source: Recorded Future)
Major ransomware-style attacks led by pro-Iranian government fronts like Moses Staff, N3tW0rm, and Agrius (Source: Recorded Future)
The report delves into an interconnected network associated with the IRGC's cyber program, revealed by a string of multi-year leaks and doxxing efforts led by anti-government hacktivists and dissident networks. Overlaps between sanctioned individuals and specific contracting parties are observed.
To read the entire analysis, click here to download the report as a PDF.