Editor's note: The following blog post originally appeared on Levi Gundert's Substack page.
 Image provided by authors
Image provided by authors
The following inspects the mechanics and economies of stolen credentials and current security approaches. We also dig into why intelligence matters greatly for enterprises committed to managing IAM cyber risk and potentially seizing competitive opportunities.
The simplest method for obtaining unauthorized access to an information system is reusing stolen credentials. Its straightforward, doesnt require technical know-how, and generally, credentials are available for almost any network or service; thus, stolen credentials remain a hot commodity. Social engineering (e.g., phishing) and software vulnerability exploitation are also effective but require more effort and investment. Threat actors (this label sounds sophisticated, but the opposite is typically true) tend toward laziness, so purchasing or otherwise acquiring stolen credentials is often the first and most desirable option.
Since the dawn of modern computing, identity verification has been a vexing challenge, and smartphones have only compounded the problem. Technology consortiums continue to push for improved standards that obviate the need for passwords. Still, static credentials are stubbornly persistent, and multi-factor authentication (MFA) options only create a sliding scale of deterrence.
 Image provided by authors
Image provided by authors
Identity Intelligence
Stolen credentials previously originated primarily from significant database breaches where passwords lived in plaintext or varying degrees of hash that were generally easy to recover. Today, credentials are stolen from web browsers via malicious infostealer code. These malware families have names like RedLine and Vidar (marketing is essential when differentiating against competitors). Infostealers have been around for a decade or more. However, recently, bad actors realized infostealers effectively obtained credentials for business systems.
Of course, there is still plenty of money in ransomware and data extortion, so its a match made in criminal heaven. These stolen credentials enable an entire ecosystem - sold in buyer-friendly markets - of derivative goods and services. Searching for and purchasing corporate credentials (SaaS, Remote Desktop, VPN, etc.) has never been easier.
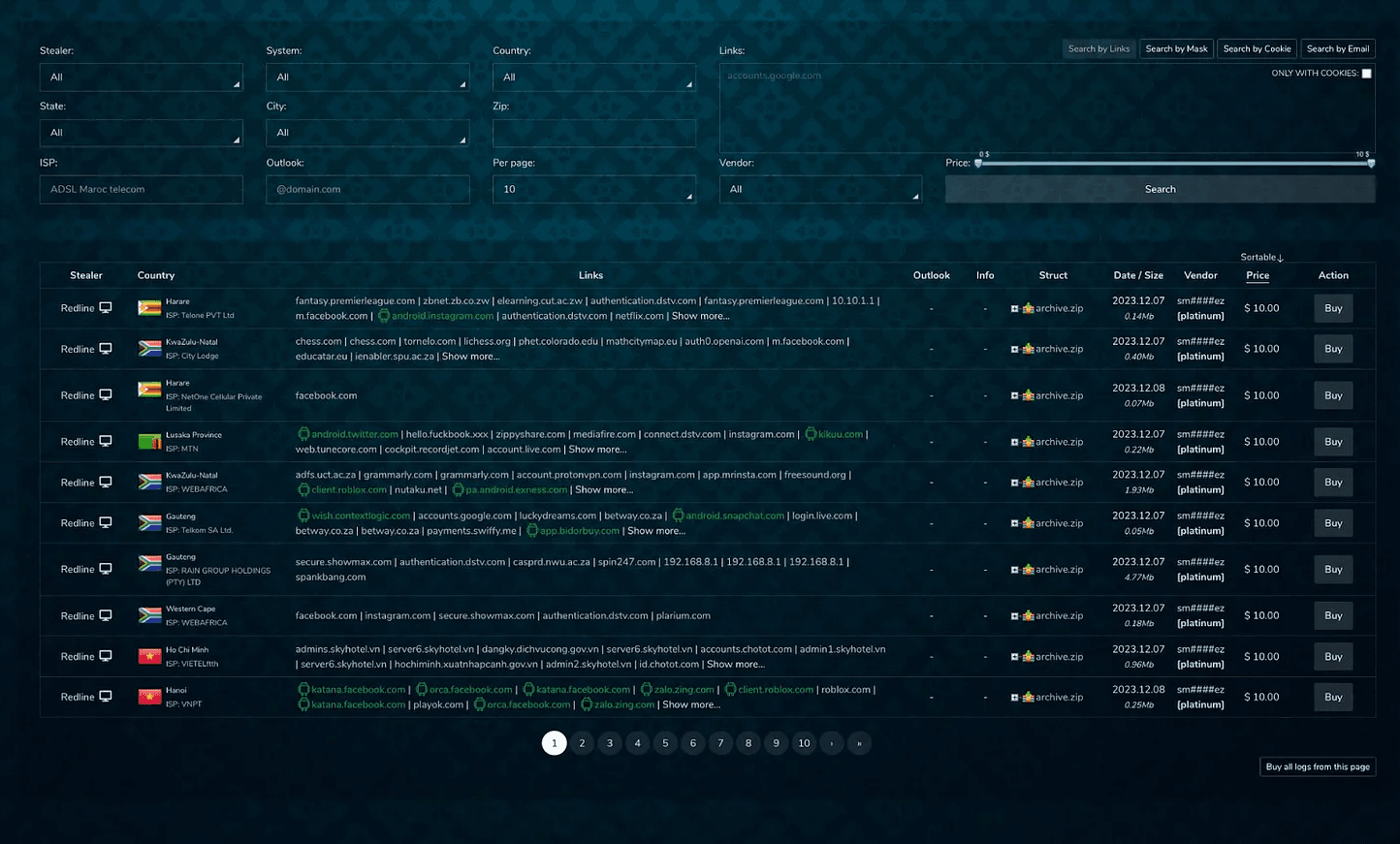 Screenshot: Russian Market, courtesy of Recorded Future
Screenshot: Russian Market, courtesy of Recorded Future
Its tempting to believe that infostealers are a fringe problem, a victim domain of the irresponsible, but the magnitude of stolen data suggests otherwise. Recorded Future detected one billion compromised credentials in the first half of 2023 alone, many of which led to significant business risk impacts. Approximately 50 credentials are stolen on average per compromised device, translating to roughly 20 million compromised devices in six months.
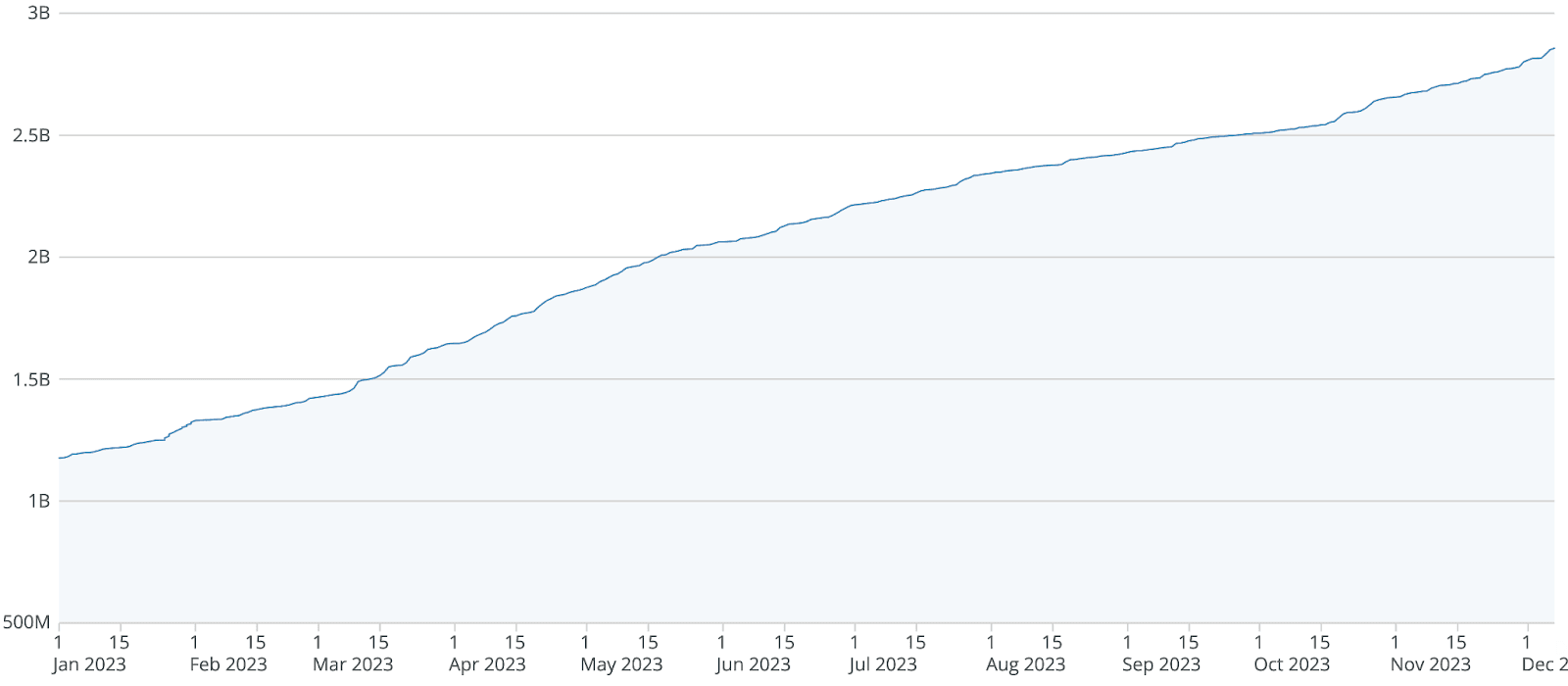 Chart: Infostealer initiated compromised credentials in 2023, courtesy of Recorded Future
Chart: Infostealer initiated compromised credentials in 2023, courtesy of Recorded Future
Of course, many of these credentials ripped from web browser authentication events lead to account takeover (ATO) of consumer services (think free movie binging, fraudulent payments, or social media contact spamming). However, enormous amounts of purloined business system credentials (e.g., VPN access, email passwords, etc.) often create derivative access to higher-value targets, like corporate infrastructure.
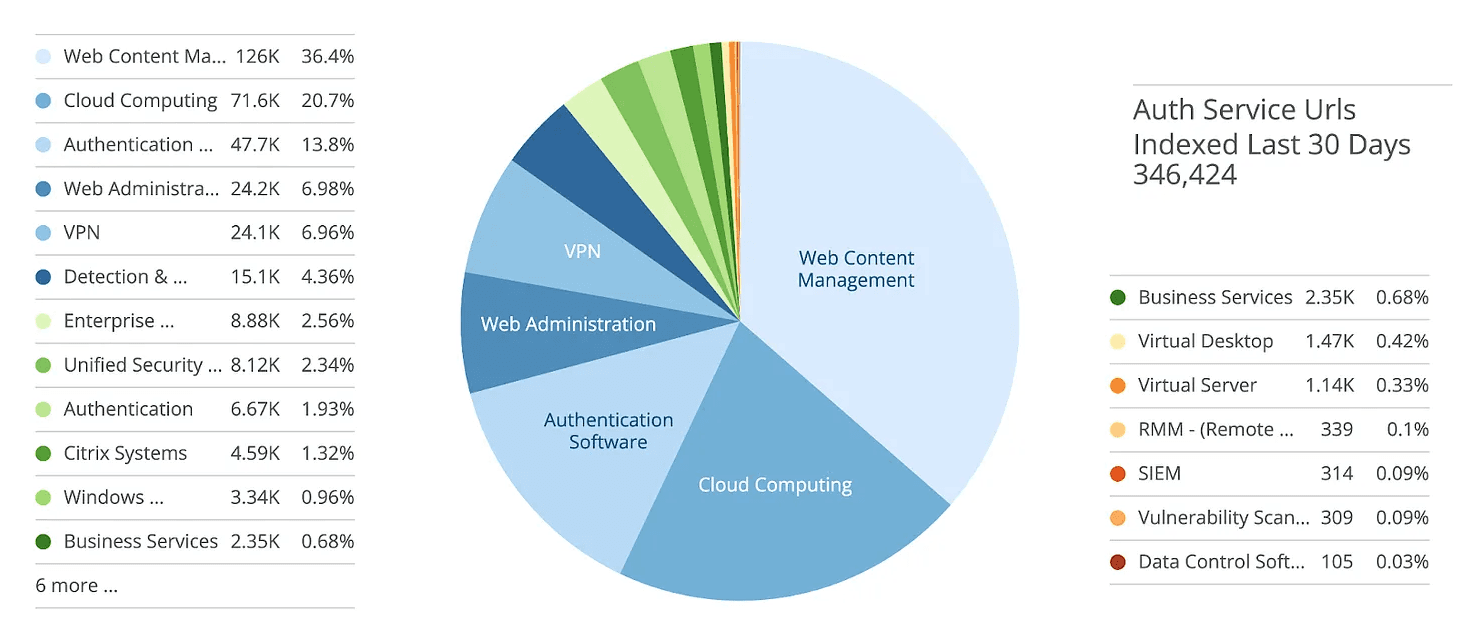 Chart: volumes of stolen credentials segmented by business system categories, courtesy of Recorded Future
Chart: volumes of stolen credentials segmented by business system categories, courtesy of Recorded Future
How does an infostealer end up on a perfectly healthy computer? Millennials that came of age during the height of peer-to-peer (P2P) file sharing - Napster, LimeWire, Gnutella, etc. (Kazaa, anyone?) remember that downloading music was treacherous, as files were often viruses in disguise. The situation hasnt changed much other than that P2P file sharing is less popular as kids now download directly from web servers, often in search of games and game add-ons. For example, when an employee takes their laptop home (or stays home post-Covid) and their child surreptitiously downloads the latest free Minecraft add-on, the installation file may include an infostealer. The infostealer works quickly, exporting pages of credentials to a central server for cataloging and sale.
Malvertising and spam also account for partial infostealer installation success. Malvertising campaigns are not limited to popular games and cheats. Malvertising also targets victims with scareware (Install this Chrome update or bad things will happen to you), running campaigns linked to trending office and productivity software, and related updates.
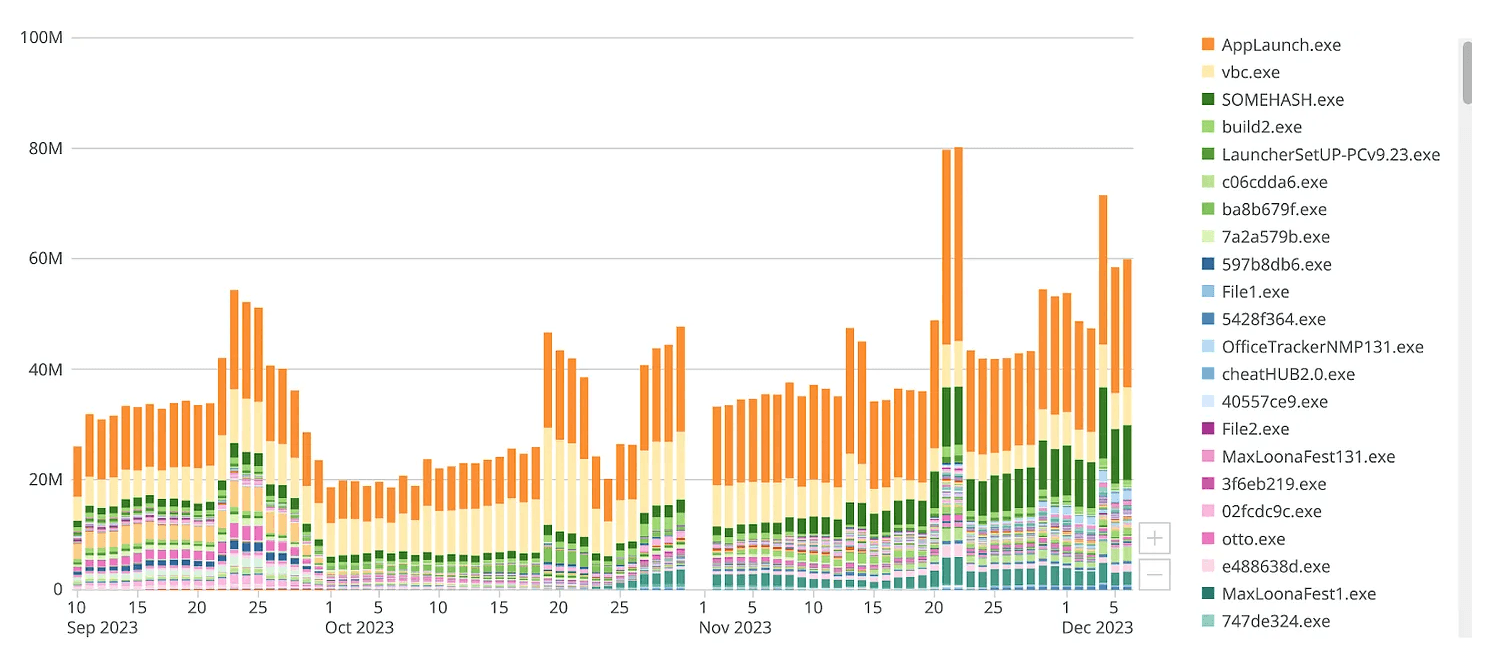 Chart: Malware filenames and malvertising campaign trends, courtesy of Recorded Future
Chart: Malware filenames and malvertising campaign trends, courtesy of Recorded Future
Tragically, anti-virus software typically does little to slow these infostealers down, as the chart below demonstrates.
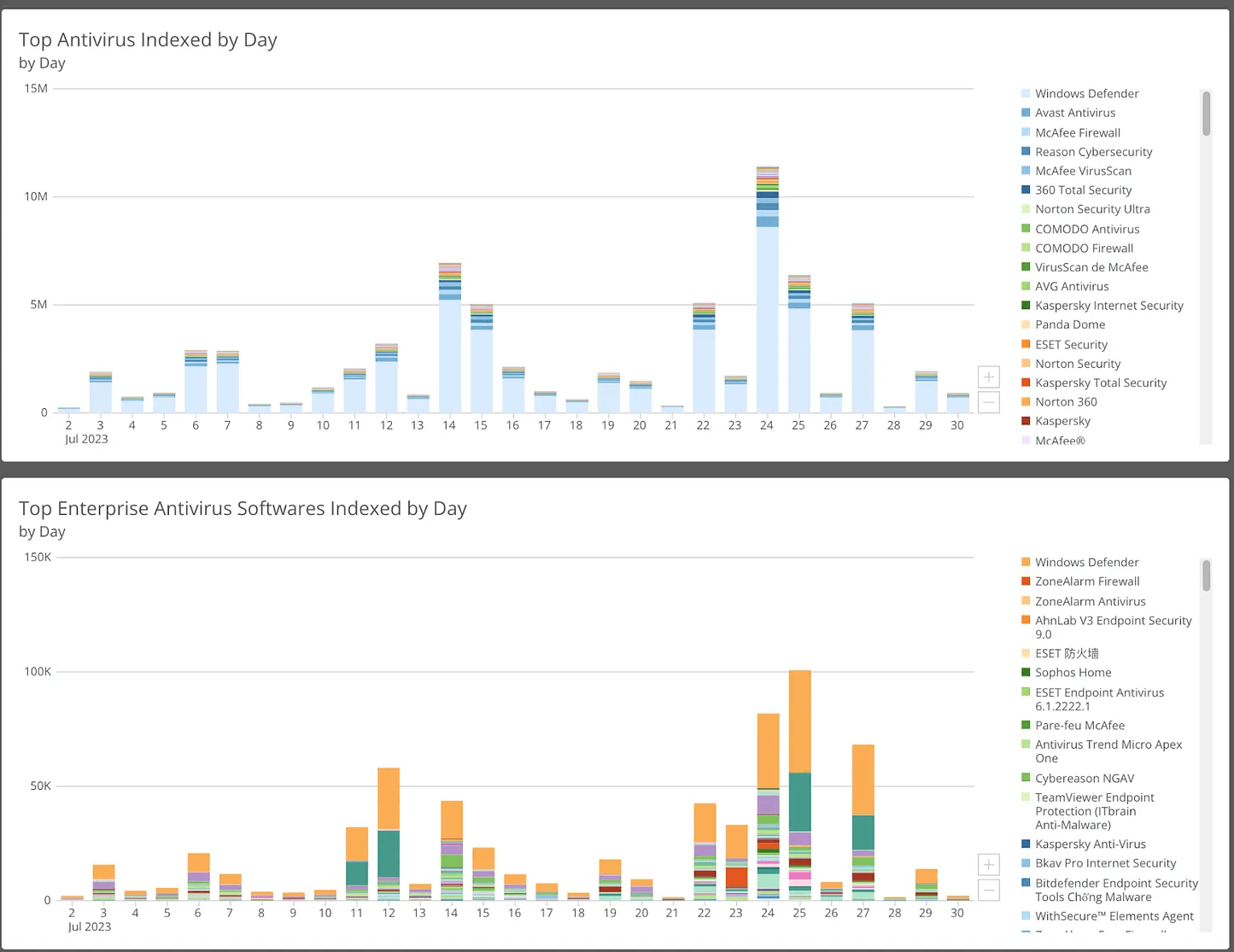 Chart: anti-virus software installed on infostealer-infected systems
Chart: anti-virus software installed on infostealer-infected systems
Security Challenges
Multi-factor authentication (MFA) has emerged as a partial identity and access management (IAM) solution in B2B and B2C, but the implementations often require meticulous oversight. Infostealers grab web session cookies and other meta-data to facilitate session cloning. SMS-delivered validation codes are susceptible to SIM swapping, and humans remain a weak point in mobile app authorization due to a desire to be helpful or eliminate nagging prompts (prompt fatigue).
On the far end of the security spectrum, hardware tokens are the most effective at preventing MFA bypasses, but they represent cultural challenges in most industries outside of technology. The overhead cost of replacing hardware tokens for remote employees when lost or forgotten is a non-starter for many businesses. The advent of passkey technology offers a promising alternative, but broad adoption will likely require a forcing function.
In addition to MFA, identity intelligence automated into IAM solutions (e.g., Microsoft Azure AD, Okta Workflows, etc.) is required for quick detection and remediation when infostealers experience success targeting employee systems.
The Risks
How should businesses think about managing IAM and the risk impacts from IAM failures?
In B2C, sponsored research suggests consumers are security conscious, particularly around ATO. Yet, where consumers have options, as in U.S. financial services, there is little incentive to care about ATO because consumers rarely bear the final cost of fraud (beyond time, which amounts to mild frustration). That paradigm is unlikely to change anytime soon.
In B2B, there is scant evidence (one recent study suggests a different conclusion) that a data breach has a long-term impact on reputation primarily because enterprise security is complex. All businesses experience varying degrees of security event impact. Even publicly traded companies dont experience sustained share price devaluation after large-scale data breaches.
A ChatGPT summary of revenue loss caused by the recent MOVEit vulnerabilities reveals even brand impairment has a short life.
The MOVEit file transfer vulnerabilities do not appear to have created significant revenue loss for Progress Software, the company behind MOVEit. According to estimates, MOVEit Transfer and MOVEit Cloud accounted for less than 4% of the company's annual revenue. Furthermore, Progress Software reported that the business impact from the MOVEit attack was minimal, despite the exploitation of a zero-day vulnerability that affected more than 2,100 organizations and exposed the data of at least 62 million people. The company reported $951,000 in expenses related to the cyber incident and vulnerability response.
However, IAM failures may cause significant legal or compliance failure risk impacts due to the increasingly aggressive evolutions of privacy-based regulatory regimes and lawsuits/class actions.
Additionally, the SECs new reporting requirements are ushering in a new age of coerced transparency. Following meaningful cyber incidents, even partial movement away from the confines of legal privilege to public reporting could usher in a new era of transparency value where robust security analytics provide evidence of risk management efforts.
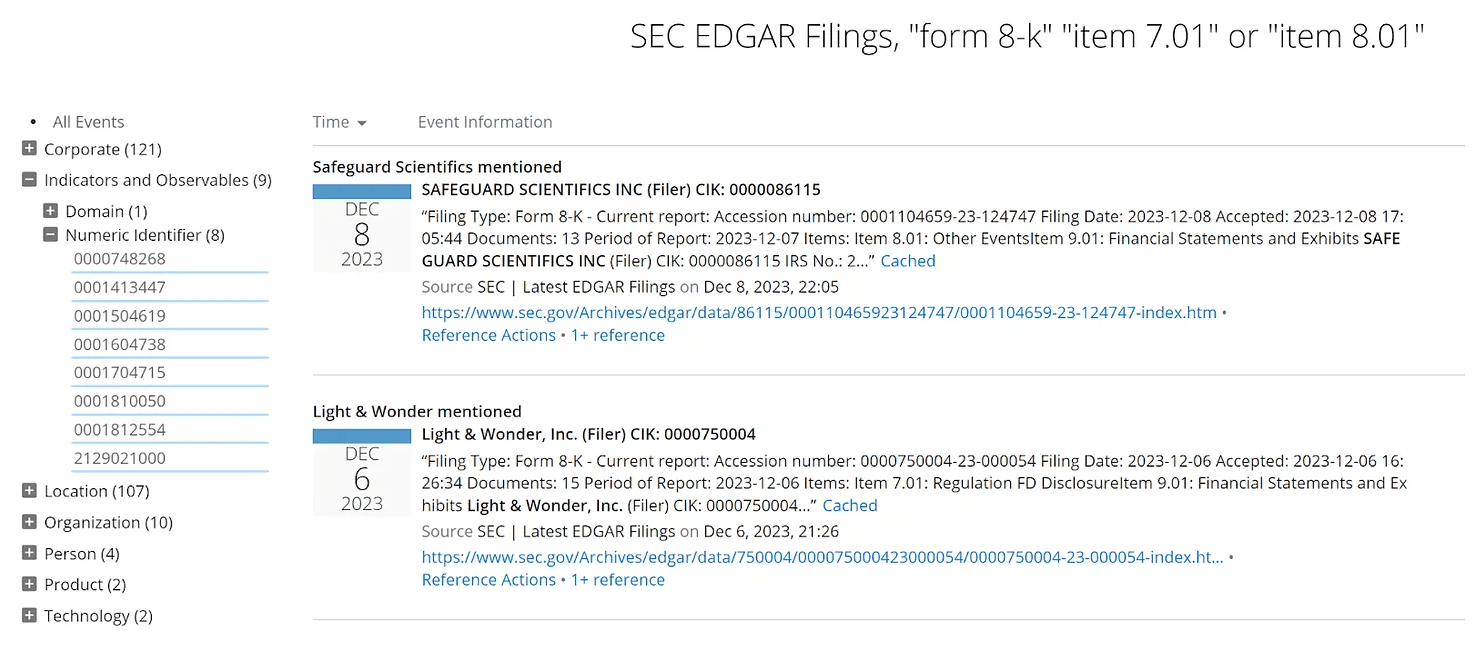 Chart: recent results for SEC form 8-k filings that contain item 7.01 or item 8.01, courtesy of Recorded Future
Chart: recent results for SEC form 8-k filings that contain item 7.01 or item 8.01, courtesy of Recorded Future
Businesses may also see an opportunity to gain a competitive advantage in crowded markets by publicly providing near real-time security analytics, which could improve security resourcing while bolstering the reputations of companies committed to transparency.
The emphasis on transparency will be particularly relevant for critical industry vendors and suppliers. One recent example is the SBOM (Software Bill of Materials) movement designed to create more transparency in software supply chains. Frequently publishing IAM security analytics would also demonstrate transparency within a long-term commitment to security and privacy, which will only help mitigate future legal or compliance risk impacts.
 Image provided by authors
Image provided by authors