
Source: Mayam studio via Shutterstock
Ransomware actors are utilizing a previously unseen tactic in their ransomware notes: posting advertisements to solicit insider information.
Researchers at the GroupSense threat intelligence team shared their findings with Dark Reading, including screenshots of the strategies these gangs are using. Groups including Sarcoma and another syndicate believed to be impersonating LockBit ransomware, known as DoNex, have adopted the strategy, the firm noted.
Part of one ransomware note includes the usual details stating that the company is in critical condition, its backups destroyed, and databases exported. Farther down in the message, however, the group states: "If you help us find this company's dirty laundry you will be rewarded. You can tell your friends about us. If you or your friend hates his boss, write to us and we will make him cry and the real hero will get a reward from us."
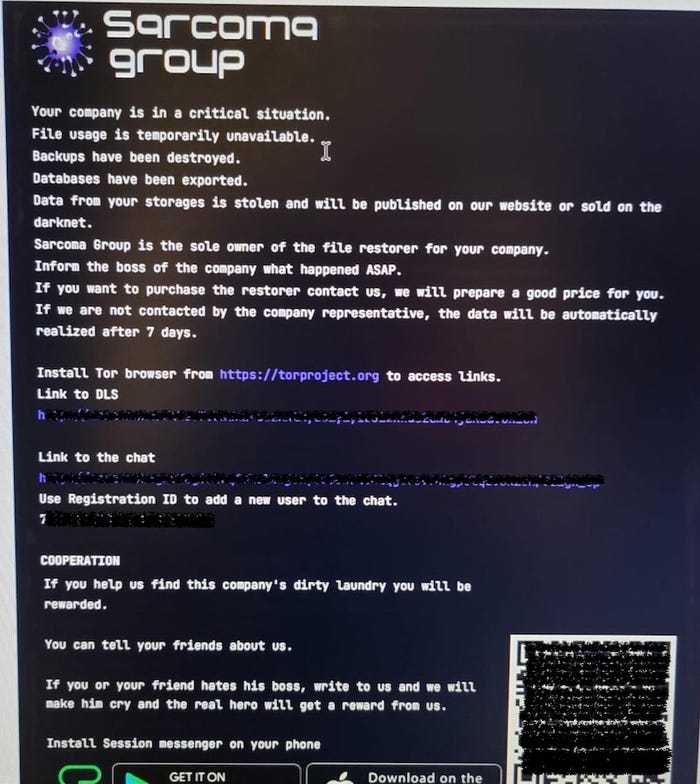
A ransom note from Sarcoma group. source: GroupSense
In a different ransom note, the threat actors write: "Would you like to earn millions of dollars $$$ ? Our company acquire access to networks of various companies, as well as insider information that can help you steal the most valuable data of any company. You can provide us accounting data for the access to any company, for example, login and password to RDP, VP, corporate email, etc. "
Related:Credential Theft Becomes Cybercriminals' Favorite Target
![Lockbitdupe-advertisement[18].jpg Lockbitdupe-advertisement[18].jpg](https://eu-images.contentstack.com/v3/assets/blt6d90778a997de1cd/bltfbaf1e2b9d6c3a53/67a146281a192e0df7556f03/Lockbitdupe-advertisement[18].jpg?width=700&auto=webp&quality=80&disable=upscale)
A ransom note from a threat group impersonating LockBit. Source: GroupSense
The threat actors then go on to detail how those who are interested can open their letter and launch a virus on their work computer. The communication is done through Tox messenger so that the users privacy is "guaranteed."
Kurtis Minder, CEO and founder at GroupSense, notes that the company sees a variety of ransom notes in the course of incident response, however, it's only been this past week that its researchers have noticed the "pseudo advertisements" at the bottom of these notes.
"I've been asking my team and kind of speculating as to why this would be a good place to put an advertisement," says Minder. "I don't know the right answer, but obviously these notes do get passed around." He notes that these threat actors may maintain a "why not" attitude toward incorporating such ads into their ransom notes. And when one ransomware actor starts a new tactic, the rest are quick to follow.
But for any individuals interested in taking up such an offer from cybercriminals, it's better to be safe than sorry.
"These folks have no accountability, so there's no guarantee you would get paid anything," Minder adds. "You trying to capitalize on this is pretty risky from an outcome perspective."
GroupSense continues to look through past ransom notes to find any earlier indication of the trend, and Minder says he expects to find more ads in addition to those already discovered.
Related:Ferret Malware Added to 'Contagious Interview' Campaign
The news comes as ransomware activity continues to grow, with cyberattackers raking in hefty profits despite a rash of law enforcement actions over the course of the past year.
 23 hours ago
2
23 hours ago
2