What is a cloud audit?
A cloud audit is an assessment of a cloud computing environment and its services, based on a specific set of controls and best practices. The audit is typically conducted by an independent third-party auditor on behalf of an organization that uses the cloud services. In some cases, a cloud audit might be carried out by the organization's own IT professionals.
When conducting a cloud audit, the auditor assesses the environment for issues such as performance, security, compliance or other concerns. The auditor then documents the results of that assessment and provides this information to the organization, along with recommendations for addressing any issues.
The goal of such an audit is to determine how well the service provider is adhering to the specified controls and best practices. To help with this process, the Cloud Security Alliance (CSA) provides auditing documents, guidelines and controls that auditors can use when examining cloud environments. Auditors commonly rely on CSA resources for their auditing tools when performing their audits.
Discussions around cloud auditing often focus only on security audits. This is because security audits can be extremely valuable in helping an organization ensure that its data is fully protected from unauthorized access and cyberthreats. However, there are numerous other types of cloud audits as well, such as performance, compliance or infrastructure audits. In some cases, an auditor will perform multiple types of audits at the same time.
How to conduct a cloud audit
Auditing a cloud environment is similar to an IT audit in many ways. Both examine a variety of operational, administrative, security and performance controls. However, a cloud audit must also take into account the unique characteristics of a cloud environment. For example, cloud platforms rely heavily on virtualization, multi-tenancy and distributed computing resources, including data storage. In addition, resources and infrastructure continuously evolve, with new elements constantly added or removed.
Cloud vendors also vary in terms of the type and number of services they offer, with services generally falling into one of three categories: infrastructure as a service (IaaS), platform as a service (PaaS) or software as a service (SaaS). A provider might offer any mix of these, and an organization might take advantage of any or all of them. At the same time, auditors might not be able to access certain information or resources because of the types of controls that providers put on their cloud environments.
Despite these challenges, a carefully conducted cloud audit can still help assure that services are delivered with the appropriate attention to specific controls, especially those involving security policies and risk management. Cloud audits look for evidence that the service provider is using best practices, complies with appropriate standards and meets certain benchmarks in delivering its services.
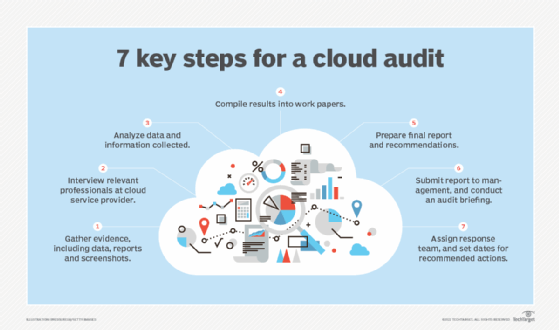 Find out the seven steps involved in an effective cloud audit.
Find out the seven steps involved in an effective cloud audit.
The exact approach that an auditor or IT professional takes when auditing a cloud environment depends in part on the type of audit being performed. Other factors might also come into play, such as the type of services being consumed or the organization's specific requirements. However, most cloud audits generally follow the same basic steps:
- Gather evidence. Collect relevant documents and other information to help understand the environment and delivered services. The evidence might include data, reports, screenshots, observations, test results or any other information useful to the investigation.
- Interview provider. Interview cloud vendor personnel about how the provider operates and delivers its services. The CSA offers cloud auditing questions and checklists that can be useful to both external and internal auditors. The CSA has partnered with ISACA to define what constitutes relevant cloud audit knowledge and to provide accreditation resources for auditors and IT professionals.
- Analyze collected data. Carefully review and assess all the collected information and interviews. Evaluate how well the cloud environment aligns with CSA and ISACA controls.
- Compile results. Combine the results of the analysis with the collected information (documentation and interviews) into a working structure that can be used to prepare a final report and recommendations.
- Prepare final report. Create the final report based on the compiled information and make recommendations based on those results.
- Submit final report. Submit the final report to the organization's management or other representatives. This is often done at the same time the auditor conducts a formal briefing about the audit's findings.
- Take action. Management develops an initial plan and timeframe for responding to the audit report and then assigns a team to respond to the report's recommended actions.
Cloud auditing tools from the CSA
The CSA provides multiple tools and guidelines for auditors and IT professionals who plan to perform cloud audits. The table below describes many of these resources and where to find them.
| Resource | Description | Link |
| Cloud Controls Matrix (CCM) v4 | Cybersecurity control framework for cloud computing aligned with CSA best practices | CCM and Consensus Assessment Initiative Questionnaire (CAIQ) v4 (downloadable document) |
| Security, Trust, Assurance and Risk (STAR) security questionnaire | Checklist tool to ask cloud vendors about security controls | STAR Level 1 Security Questionnaire (downloadable document |
| STAR Registry | List of cloud vendors' security and regulatory compliance postures | STAR Registry (web listing) |
| CSA best practices | Guidance on cloud security, performance and auditing | CSA Security Guidance (downloadable document) |
| Mapping to other standards | Mapping CCM v4 to other industry standards, such as the International Organization for Standardization 27000 series and Payment Card Industry Data Security Standard | Included in CCM and CAIQ v4 |
| Controls Applicability Matrix | Help for auditors to decide the most appropriate controls to use for a specific vendor | Included in CCM and CAIQ v4 |
| CCM Metrics | Compendium of security metrics for clouds to support governance, risk and compliance activities | Included in CCM and CAIQ v4 |
| CCM v4 Implementation Guidelines | Guidelines for using the CCM v4 audit standards | Included in CCM and CAIQ |
| Continuous Audit Metrics Catalog | Guidance to plan and implement continuous cloud audit activities | Continuous Audit Metrics (downloadable document) |
| CCM v4 Auditing Guidelines | Guidance for planning, organizing and conducting a cloud audit engagement using CCM v4 | CCM Auditing Guidelines (downloadable document) |
Cloud audit professional credentials
In 2021, the CSA and ISACA jointly launched the Certificate of Cloud Auditing Knowledge (CCAK), a vendor-neutral technical credential for auditing cloud environments. The CCAK builds on the CSA's Certificate of Cloud Security Knowledge (CCSK). The CCSK provides a widely recognized standard for expertise in cloud security, while promoting an understanding of how to secure cloud data. A CCSK certificate is often the first step an auditor takes in preparing for cloud auditing.
The CCAK expands on the CCSK by providing a set of essential principles for auditing cloud computing systems. The CCAK helps to prepare IT and security professionals for conducting audits so they can better ensure that internal requirements are fulfilled and appropriate controls are in place. To this end, the CCAK trains these professionals in how to objectively evaluate critical cloud assurance issues.
The CCAK complements ISACA's ANSI-accredited certifications, which include the Certified Information Systems Auditor (CISA). Together with the CCSK, the CCAK provides evidence of an auditor's knowledge of cloud infrastructure and systems, including security and vulnerabilities. It also demonstrates that the auditor knows how to conduct a cloud audit.
Explore 10 cloud security certifications (including CCAK and CCSK) to boost your career. See how to approach cloud compliance monitoring.
This was last updated in March 2024
 11 months ago
32
11 months ago
32







