The notorious Cl0p ransomware group will soon name more than 60 organizations that were hacked recently through the exploitation of vulnerabilities in file transfer products from enterprise software developer Cleo.
Cl0p took credit for the Cleo attacks in mid-December, telling SecurityWeek at the time that they had hit “quite a lot” of targets as part of the campaign.
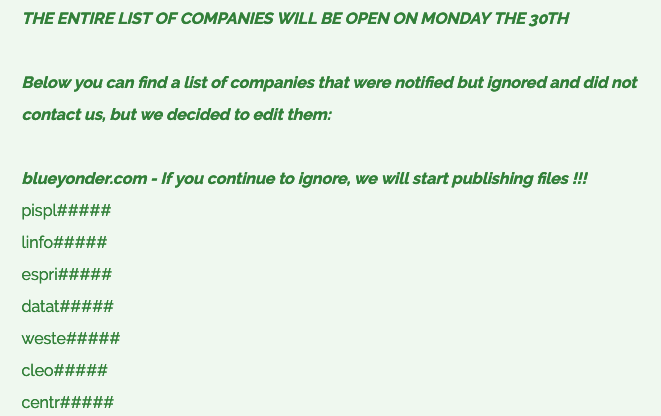
The ransomware gang has now published an announcement on its Tor-based website, telling victims that they are being contacted and provided access to a secret chat, as well as proof that data has been stolen from their systems.
Only one victim has been named to date: supply chain management software provider Blue Yonder. More than 60 other partial company names have been listed on Cl0p’s website and their full name will be revealed on December 30, unless they pay a ransom.
According to the cybercriminals, these victims have so far ignored them and they are now being given a last chance.
There has been strong suspicion that the Blue Yonder attack, which hit Starbucks and some major grocery store chains, was carried out through Cleo exploitation.
However, a new ransomware group named Termite has taken credit for the Blue Yonder attack and there has also been strong suspicion that Termite was behind the Cleo attacks. All this reinforces theories about a connection between Cl0p and Termite.
Cl0p’s new post suggests that Blue Yonder has been ignoring communication attempts from the cybercriminals.
The Cleo attacks have involved exploitation of two vulnerabilities affecting the Harmony, VLTrader, and LexiCom file transfer tools. Harmony, VLTrader and LexiCom versions 5.8.0.24 patch the vulnerabilities, which are tracked as CVE-2024-50623 and CVE-2024-55956.
Advertisement. Scroll to continue reading.
The vulnerabilities allow unauthenticated attackers to steal files from the targeted system, and at least CVE-2024-55956 appears to have been exploited as a zero-day. Attacks exploiting the flaws have been seen since December 3.
It’s possible that other threat groups have been exploiting the Cleo vulnerabilities as well since their existence came to light.
Cleo has more than 4,000 customers and there appear to be hundreds of internet-exposed instances of its file transfer products.
Cl0p was also responsible for the MOVEit campaign, in which the group exploited a zero-day in the MOVEit file transfer software to steal information from thousands of organizations.
Related: Undocumented DrayTek Vulnerabilities Exploited to Hack Hundreds of Orgs
Related: CISA Urges Immediate Patching of Exploited BeyondTrust Vulnerability
Related: CISA Warns of Exploited Adobe ColdFusion, Windows Vulnerabilities
 1 month ago
25
1 month ago
25