The Cleafy threat intelligence team recently came across an Android banking trojan that has been observed targeting users in Europe and elsewhere.
The cybersecurity firm noticed in late October that there had been a significant increase in what initially appeared to be a campaign involving TgToxic, a China-linked piece of malware that has been used since at least mid-2022 to target Android users in Southeast Asia in an effort to steal cryptocurrency and funds from banking and other finance apps.
However, a closer analysis revealed differences in the code and Cleafy started tracking the new malware as ToxicPanda.
According to the online fraud management and prevention firm, ToxicPanda has remote access trojan (RAT) capabilities, enabling the attackers to conduct account takeover (ATO) through a technique known as on-device fraud (ODF).
ODF involves initiating transactions on the compromised device and stealthily modifying account settings, allowing the hackers to conduct malicious activities without triggering the security mechanisms put in place by banks, including identity verification and behavior-based fraud detection. Cleafy has identified 16 financial institution apps targeted by ToxicPanda.
The Android trojan can intercept one-time passwords received by the device via SMS or ones generated by authenticator apps, which allows the cybercriminals to bypass multi-factor authentication.
The malware obtains elevated permissions, can manipulate user inputs, and capture app data by abusing the accessibility services in Android.
ToxicPanda appears to have been around since early or mid-2024 and an analysis of its source code has shown that it’s still in development, with some commands yet to be working.
Advertisement. Scroll to continue reading.
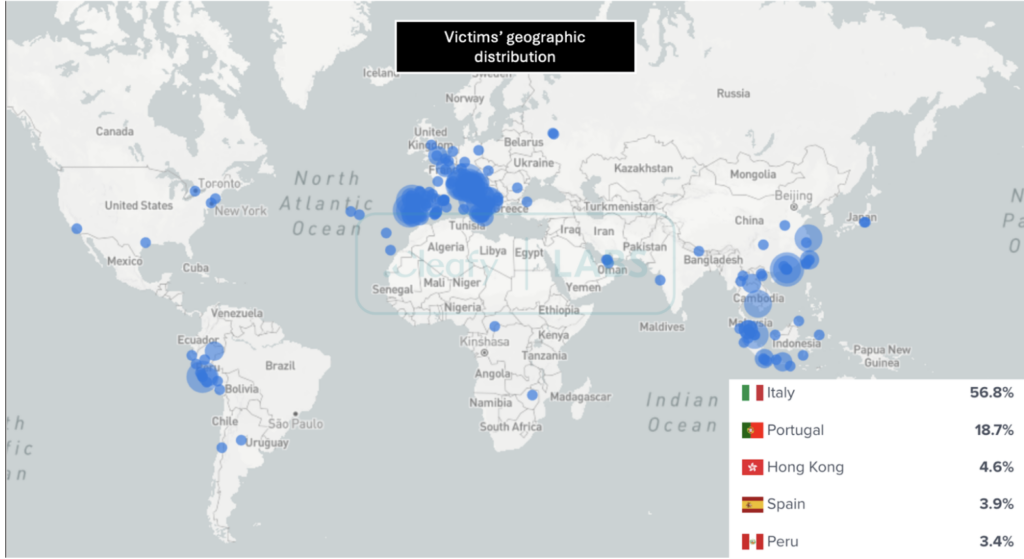
An analysis of the ToxicPanda infrastructure gave Cleafy researchers access to a command and control (C&C) panel, which revealed a botnet of more than 1,500 compromised Android devices. More than half of the infections were seen in Italy, followed — in Europe — by Portugal, Spain and France.
Some infections were also observed in Peru and other Latin American countries, suggesting that the cybercriminals are further expanding their operation. Similar to TgToxic, victims were also seen in Southeast Asia.
The security firm has determined that — also similar to TgToxic — the threat actors behind ToxicPanda are likely Chinese speakers.
“In this case, visibility into the botnet’s control panel confirmed that the ToxicPanda campaign was orchestrated by a Chinese-speaking group—a rare occurrence in Europe, where this campaign has primarily occurred,” the company noted in a blog post on ToxicPanda.
Cleafy concluded, “More broadly, we observe a marked shift as Chinese-speaking TAs expand their focus into new geographical regions, especially targeting financial institutions and customers in pursuit of banking fraud opportunities. This trend underscores the mobile security ecosystem’s escalating challenge, as the marketplace is increasingly saturated with malware and new threat actors emerge.”
Related: Massive OTP-Stealing Android Malware Campaign Discovered
Related: ‘Vultur’ Android Malware Gets Extensive Device Interaction Capabilities
 3 months ago
25
3 months ago
25