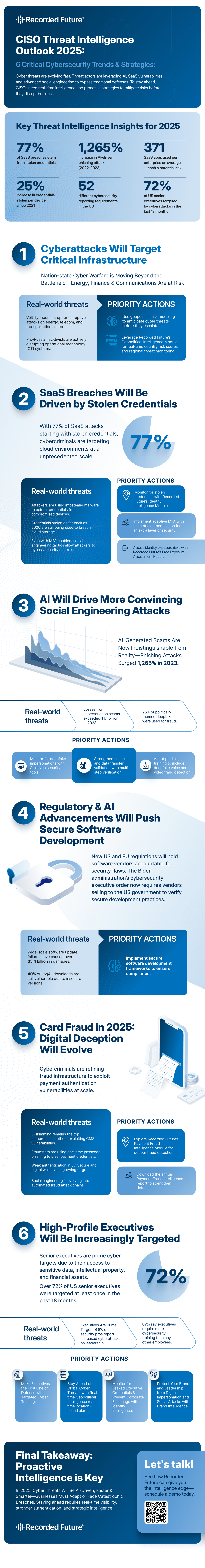
As threat actors continually adopt new tactics using everything from generative AI to popular SaaS applications to e-skimmer kits CISOs and their teams need the latest and most in-depth threat intelligence to stay one step ahead. Explore Recorded Futures top threat intelligence outlooks for 2025, as well as research and strategies to help you see threats before they disrupt your business.
Key Statistics
- 77% of SaaS attacks begin with stolen credentials
- 1,265% increase in AI-enabled phishing attacks (2022-2023)
- 371 was the average number of SaaS apps per enterprise
- 25% increase in credentials stolen per device since 2021
- 52 different incident reporting requirements across sectors in the US
- 72% of US senior executives are targeted by cyber threats at least once (December 2022May 2024)
Outlook #1: Expanding the cyber battlefield will put infrastructure at risk.
Cyber attacks are becoming the weapon of choice for disrupting (or threatening disruption) in rival nations even outside of conflict zones. This not only impacts critical infrastructure directly, but also could lead to secondary disruptions at organizations that depend on that infrastructure.
Real-world threats:
- Volt Typhoon pre-positioning for disruptive attacks in energy, communications, and transportation sectors
- Pro-Russia hacktivists virtually manipulating operational technology systems
Priority actions:
CISOs must understand how geopolitical events affect their security posture to manage risk and communicate with their boards effectively.
- Use strategic foresight techniques, including Horizon Scanning, PESTLE-M, and the Cone of Plausibility, to understand the external environment, anticipate whats ahead, and make better intelligence-informed decisions
- Explore Recorded Futures Geopolitical Intelligence Module, which includes a Country Risk Scores help you understand and prioritize risks associated with operating in different countries.
Outlook #2: SaaS will make it easier to weaponize stolen credentials.
Cybercriminals are increasingly targeting interconnected software-as-a-service (SaaS) applications to gain access to enterprise ecosystems. With the average organization now using approximately 371 SaaS apps, and with 77% of SaaS app attacks beginning with stolen credentials, its essential to prioritize identity security.
Credentials are frequently stolen by information-stealing malware, or infostealers, that are built to target a variety of operating systems and mobile devices. Per Recorded Future research, credential theft per device has risen 25% since 2021, increasing the risk of unlocking valuable corporate assets or credential stuffing attacks.
Real-world threats:
- The recent high profile breaches have used credentials stolen from infostealers from as far back as 2020 to gain access to over 165 companies cloud storage instances.
- Even with MFA, threat actors were able to use subtle social engineering strategies,to gain access to corporate systems.
Priority actions:
- Consider AMFA with biometric authentication to provide an extra layer of protection from unauthorized access.
- Use Recorded Futures Identity Intelligence Module to track stolen credentials for your organization
- Reach out to learn more about your organizations identity exposures with our free Exposure Assessment Report.
Outlook #3: Generative AI will transform social engineering.
The reported 1,265% increase in phishing attacks between Q4 2022 and November 2023 has been attributed to the public release of LLMs like ChatGPT. Spear phishing attacks have become more dangerous now that threat actors can use generative AI to quickly create highly targeted and convincing messages as well as deepfake phone calls and videos (TechTarget).
In addition to phishing, the increasing availability of sophisticated faceswap and other deepfake technology means more threat actors will be able to produce believable impersonations of company executives, celebrities, and political figures, pulling off increasingly costly scams.
Real-world threats:
- Losses to impersonation scams topped $1.1 billion in 2023.
- 26% of politically themed deepfakes were used to commit fraud.
Priority actions:
- Adapt phishing training to include detecting voice and video fraud
- Ensure processes for transferring money or data are resilient to scams by increasing validation checkpoints and educating employees on suspicious requests
Outlook #4: Regulatory demands and AI capabilities will push demand for safer code.
New regulations in both the US and EU are pushing software companies to prioritize security. One of the last Biden-era cyber executive orders requires software vendors selling to the US federal government to verify they are using secure software development practices. Meanwhile, the EU amended liability laws seek to hold software companies accountable for harm caused by their products.
Real-world threats:
- Recent wide-scaled outages caused by defective code in a software update, have caused over $5.4 billion in damages.
- 40% of Log4J downloads are vulnerable to exploitation as a result of developers downloading insecure versions
Priority actions:
- Ensure your organization is incorporating secure software development frameworks into their operations
Outlook #5: Card fraud in 2025: digital deception will evolve.
Card fraud is a global, professional ecosystem where cybercriminals specialize in compromising and monetizing payment data through sophisticated digital channels. Attackers are shifting to more nuanced digital strategies that exploit authentication vulnerabilities and create seamless fraud infrastructure.
Real-world threats:
- E-skimming remains the primary compromise method, leveraging easy-to-use kits and CMS vulnerabilities
- Scam websites will employ advanced tactics, such as one-time passcode phishing, to facilitate card theft and enhance their ability to monetize the stolen data more efficiently
- Fraudsters will target weak authentication in 3D Secure and digital wallets
- Social engineering tactics will be scaled into systematic cyber fraud attack chains
Priority actions:
- Explore Recorded Futures Payment Fraud Intelligence Module.
- Download our newly published annual Payment Fraud Intelligence report to protect your business and customers.
Outlook #6: High-profile executives will be increasingly targeted.
With broad authority over their organizations data, IP, and money, senior business executives have become major targets of digital threats, cyberattacks, and privacy invasions. In fact, according to a survey of IT and cybersecurity professionals, 72% of senior executives in the US were targeted at least once in the 18 months prior to May 2024.
Real-world threats:
- 69% of surveyed IT and cybersecurity professionals whose companys senior executives were previously targets say cyberattacks against senior staff members have increased.
- 87% of the same professionals agree that senior executives should receive more cybersecurity training than other employees.
Priority actions:
- Step up training for senior leaders to reinforce cyber safety best practices.
- Use Recorded Future Identity Intelligence to monitor for leaked credentials, doxing incidents, or PII exposure across dark web and messaging platforms.
- Use Recorded Future Geopolitical Intelligence for real-time geofence alerting as well as country risk scoring and local event detection for travel risk assessments.
- Use Recorded Future Brand Intelligence for digital footprint auditing, impersonation detection, and social media threat detection.