
Source: Quality Stock via Alamy Stock Photo
Researchers have developed a simple exploit capable of unlocking all of the doors at more than 10,000 hotels worldwide.
Saflok-brand RFID-based keycard locks have been around for 36 years. But only in the late summer of 2022 did a team of seven researchers identify a series of vulnerabilities that allowed hackers to crack them open, deadbolt and all, using only a customized keycard.
Saflok locks are installed on more than 3 million doors across 13,000 hotels and multi-family housing environments in 131 countries. Dormakaba began rolling out a patch last November but, to implement it, each device needs to be updated one by one. As of this month, just 36% of affected locks have been updated or replaced.
It's the latest problem for an industry facing uniquely difficult security challenges.
"Important people stay in hotels, and hotels maintain sensitive data about their guests," notes Lee Clark, manager of cyber threat intelligence production at the Retail and Hospitality ISAC. "So if you run a nice hotel, you're up against nation-backed threat actors that are looking, for cyber-espionage purposes, to steal information about important people. And especially for organizations that are attached to gaming facilities, there's a lot of money at stake."
How to Break Into Millions of Hotel Rooms
Breaking into unsuspecting travelers' hotel rooms requires just a few items.
First: any keycard from the targeted property — your own room key, someone else's, even an expired one in the garbage.
You'll also need another two MIFARE Classic keycards (the kind used by Saflok) to write to, and any one of a number of commercially available products capable of doing that job: a Proxmark3, Flipper Zero, or even an near-field communication (NFC)-capable Android phone.
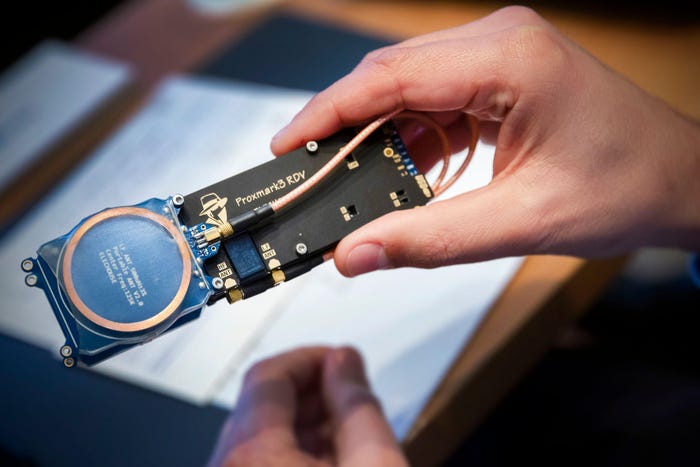
Proxmark3, Source: Guido Schiefer via Alamy Stock Photo
The team behind "Unsaflok" are keeping close hold over specifics for now, but the outline of how their attack works is as follows.
First, a code from the hotel card is recorded by the read-write device. Then, the attacker writes to the other two cards. The first custom card, when tapped against a Saflok lock, overwrites a crucial piece of its data, and then the second custom card can be used to unlock the door.
It may take a while for this exploit to be fully stamped out globally. Some connected locks sold in recent years can be updated via a front desk management system. But for the majority of Safloks around the world, the researchers explained, "Upgrading each hotel is an intensive process. All locks require a software update or have to be replaced. Additionally, all keycards have to be reissued, front desk software and card encoders have to be upgraded, and third-party integrations (e.g., elevators, parking garages, and payment systems) may require additional upgrades."
Particularly concerned guests can determine whether their hotel room door is vulnerable using the NFC Taginfo app on iOS and Android, which identifies different types of keycards. Updated Saflok locks use MIFARE Ultralight C cards, instead of MIFARE Classic.
Other Ways to Do It
As effective as Unsaflok is, Clark notes, "It's a new play in an old game — there are a lot of similar methods to unlock electronic locks."
At Black Hat 2019, for example, two members of the Chaos Computer Club undermined a mobile phone keycard system used by an EU hotel. Even more dangerous proofs-of-concept had been demonstrated much earlier still.
In fact, just a couple of months ago — and not for the first time — Saflok's key derivation function (KDF) was reverse engineered, opening the door for hackers to read and clone keycards.
The simplest way to unlock a hotel door, though, is probably with a Flipper Zero. "It's an interesting little multitool — it looks like a Game Boy," Clark explains. "It can do a number of things that help with penetration testing, and one of the things that it can do is open hotel locks.
"And this is all if you don't want to just kick open the door with your foot, right?"
In the face of all of these potential threats, though, there is good news.
How Hotels Secure Their Doors
Hoteliers have plenty of means for protecting guests from potential intruders.
Of course, there's physical security: cameras in hallways, training staff to watch out for suspicious activity, automatic locking mechanisms that trigger a few seconds after a guest opens their door.
Particularly sophisticated hotels can also incorporate security detection into broader building automation management systems, Clark explains, "because a smart lock is really just part of a hotel's overall [Internet of Things] system, which also involves the stuff for maintaining the temperature and chemical levels in the pool and the spa, temperatures and humidity levels in the hotel rooms, etc."
Securing hotel locks beyond this point, however, can get dicey.
"There are a few schools of thought around better securing these locks," Clark notes, for example, "by implementing multifactor authentication where possible. That one can be questionable, because you're putting a barrier between the guest and the convenience of easily opening their room. Password protections are another one, but that comes with all the regular risks of potentially weak passwords. A big one lately has been biometric locks — adding a fingerprint or something like that to the locks — but then there's the question of storing that biometric data, which brings up other risks and regulatory issues."
For guests who aren't comforted by the existing state of hotel security, there is one way to prevent even the most sophisticated attackers from breaking into your room, at least when you're inside of it: a good old-fashioned chain lock or swing bar.
 1 month ago
11
1 month ago
11